Is (Wipe the content) the same as (Secure Delete)?
If you've been using AB Commander to manage your files and folders, you've probably noticed the Wipe the content option available on the Delete window (that appears when you choose the Delete command from the menu of AB Commander):
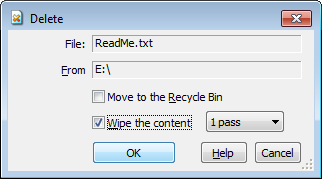
You've been probably wondering, why would you need that option? Isn't the Delete command supposed to do that by itself?
To understand the need for this option, let's consider what happens under the hood when you delete a file. If you use Windows Explorer to delete a file on a drive that has a Recycle Bin on it, then the file is not deleted at all! Instead, Windows moves it to the Recycle Bin, giving you (or someone else who gets hold of your disk) the possibility to restore the file you've "deleted". The same happens when you delete the file with AB Commander and select the Move to the Recycle Bin option on the Delete window.
If you do not select the Move to the Recycle Bin option (or, if the file is located on a drive that does not have the Recycle Bin), then the deletion occurs differently: instead of moving the file to the Recycle Bin, Windows marks the blocks of the hard drive space occupied by the file as available for use by other files. That is, even though the file disappears from the file listings, its content still remains on the disk! That's what makes the undelete programs possible: they work by analyzing the internal structures that Windows keeps on the disk and use that information to reconstruct the files deleted in this way. If the file has been deleted only a few minutes ago and you have not created any new files yet, there is a good chance to undelete the file in this way.
In any case, the important fact about deleting a file without moving it into the Recycle Bin is that the content of the file is not getting destroyed and there is a possibility to reconstruct it (or a part of it), even after the file has been deleted. What if the file contains sensitive information that you want to actually be destroyed? That's what Wipe the content option is for. If you select this option, then before deleting the file, AB Commander wipes its content by writing constant bytes over the actual data the file contains. This way, if someone gets hold of your disk and uses an undelete program to recover the file you've deleted, the recovered file would contain the bytes written over by AB Commander when wiping the file, rather than the original content of the file.
The bytes used to wipe out the content of the files depend on the number of passes you select next to the Wipe the content option. If you select 1 pass, then AB Commander replaces each byte of the file content with 0. For the majority of the real world situations this would be enough to prevent someone from recovering the contents of the deleted file.
There are ways to analyze the physical structure of the magnetic matter of the disk plates used to store the information and recover the bits and bytes that were overwritten with 0s though. (This would be the case of you vs the NSA/CIA/FBI kind of a situation.) To make it much more difficult to conduct such an investigation, you may want to select the 3 passes option, in which case AB Commander overwrites each byte 3 times. The first pass uses the byte 0x55 (which happens to have the binary representation of 01010101), the second pass uses the byte 0xAA (or 10101010 in the binary presentation), and the third pass uses the byte 0. Of course, keep in mind that using the 3-pass wiping takes 3 times as long to complete. And if you are really concerned about the NSA/CIA/FBI getting hold of your files, then a physical destruction of the disk would probably protect your files better.
Now, if this procedure prevents the recovery of the deleted files, "Why don't you call this option Secure Delete then, like many of your competitors do", you might be wondering? Well, because "secure" is a strong word and we would rather use it only when something is really secure. Unfortunately, there are situations when the Wipe the content option may not produce the intended result. For example, if the file you want to erase is located on a SSD or a flash drive, there is a good chance that the drive controller uses the wear-leveling techniques, to extend the useful life of the device. It means that when the content of a file is overwritten, the new bytes may be written to a block of the drive's space other than that of the original file. In such a case, even if you select the 3-pass wipe option, each pass would be written to a new set of the drive space blocks, and no wiping of the content would actually occur. Calling such an operation "secure" would be very misleading.
Even if the drive does not use the wear-leveling, there is a possibility for the original content of the file to leak even after its content has been wiped. For example, when you save a file after editing it, many programs do not write the new content directly over the exiting data. Instead, they first create a temporary file, write the new content in it, and after making sure the file has been created successfully, they delete the original file, and rename the new file back to the original. (It may all happen in the background, without you noticing it). The result is, the previous content of the file is still available on the drive, even if you don't see it. If you wipe the content of the file you've just saved, you would wipe only the latest version of it, while the previous version would still be available for the undelete utilities to recover. Again, we would not want to use the word "secure" for the option that may provide an insecure result.
![]() Take control of your files and folders with AB Commander file manager for Windows 11, 10, 8, 7.
Take control of your files and folders with AB Commander file manager for Windows 11, 10, 8, 7.
User rating: ![]() 4.8 / 5
4.8 / 5
Purchase
or
download a free trial.
Read more...
OK, if secure delete of files is not reliable, what should you do if you really want to make sure the file cannot be recovered no matter what? Well, the only 100% option is to physically destroy the drive. (Although that may not be easy: if you ever tried to disassemble a hard drive you know what I mean!). If physical destruction is not an option, the next best thing is to securely erase the whole drive. Go to the web site of the manufacturer of your drive and search for a secure erase utility in the Downloads or Support section: you may find such a utility offered by the manufacturer tailored specifically to your drive.
The third best option is to do a "full" (rather than "quick") format of the drive, using the Windows drive formatting tools. (See Windows Help for more information what your version of Windows has to offer in this regard). When Windows does the full format, it erases every part of the drive, including any previous versions of the files that might be lying around. While it may not stop a determined forensic analyst, the full format should prevent the regular undelete tools from recovering your files.
AB Commander User's Guide • Download • Purchase
If you want to link to this article, you can use this HTML code: <a href="https://www.winability.com/wipe-the-content-vs-secure-delete/">Is (Wipe the content) the same as (Secure Delete)?</a>
More information
- What people are saying about AB Commander...
- A FREE 30-day license is included
- What's new in the new version
- End User License Agreement (EULA)
- Space Investigator
- Using DiffMerge as the external tool of AB Commander
- Is "Wipe the content" the same as "Secure Delete"?
- How to start programs elevated from a batch file
- How to make elevated programs recognize network drives
- How to disable hibernation
- How to set up Notepad++ as the external text editor for AB Commander
- Integrating AB Commander with Universal Viewer
- How to repair Windows desktop icons with AB Commander
- How to show drive letters first in AB Commander and Windows Explorer
- Organize your photo library with the Rename tool of AB Commander
- How to move images from an Android device to PC
- How to synchronize images between a PC and an Android device
- Using junction points to change the iTunes backup folder location
- Always have a backup of your important files

 Stand with Ukraine
Stand with Ukraine

