Recovering the password of a Virtual Encrypted Disk |
Previously we've discussed the "spare key" option that could be of help if you forget the password for an encrypted disk of yours. However, what if you did not select the option to create a "spare key" the on your computer, or if you have replaced your computer at some point and the original "spare key" file is no longer available? Here comes the last resort, the command to recover the lost password, by trying all possible passwords from a specific set of characters, one at a time, until the one of them happens to match the original password.
To get to the password recovery command, start as usual, by running USBCrypt and getting to the point where the password prompted appears in order to start the Virtual Encrypted Disk. Click on the Tools button, and the menu will be shown with the Recover Password command on it:
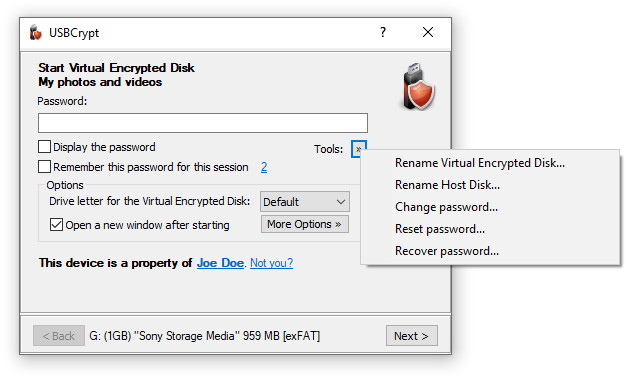
If you choose the Recover Password command, you will be presented with the following window that asks you to specify the kind of passwords you want to try:
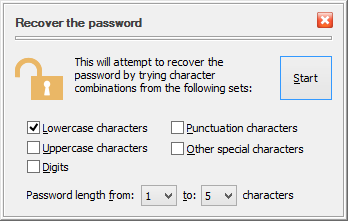
You can specify the minimum and maximum lengths of the passwords, as well the character sets to use when trying the passwords. For example, if choose only the lowercase characters, the minimum lengths 1, and the maximum length 3, then USBCrypt will start applying the 1-character lowercase passwords: a, b, c, and so on, down to z. Each such password would be tested against the current Virtual Encrypted Disk. After all 1-character passwords have been tried, USBCrypt will begin to try the 2-character ones: aa, ab, ac, and so on, down to zz. If none of them unlocks the Virtual Encrypted Disk, it will then try all possible 3-character passwords, until one of them is detected to be able to unlock the Virtual Encrypted Disk (if any).
If you try the Recover password command, you will see that trying each possible password combination in turn takes some time, depending on the speed of your computer. USBCrypt estimates the time that is necessary to try all possible passwords from the set you've defined and displays that estimate on the progress window for you:
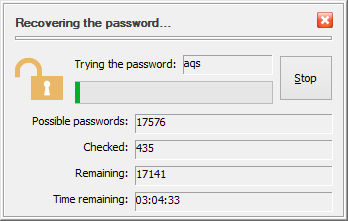
Of course, the estimate depends on the processor speed of your computer. Try it and see for yourself. That could be a good illustration fn the importance of choosing the strong passwords. For example, the amount of time to try all possible 3-character lowercase passwords on a 2GHz dual-core processor is about 2 hours. If you recall that that's exactly how the evaluation passwords are imitated, you will see that if you use USBCrypt in the evaluation mode, anyone should be able to start your Virtual Encrypted Disk by running the recovery password procedure for a mere couple of hours.
If you have purchased a license for continued use of USBCrypt, then the evaluation passwords are not created for your encrypted drives and the strength of the protection is determined exclusively by the complexity of the passwords that you've chosen. For example, on the same processor, to try all possible 5-character passwords that may contain both the lowercase and the uppercase characters as well as digits and special characters, it would take about 30 years to actually try them all. Someone must want to get to your encrypted files badly enough to wait that long! Of course, if someone wants to know your secrets that bad, she could purchase 30 computers and run them simultaneously and that would make her able to recover your password in just one year. Keep that in mind when deciding whether your password is strong enough!.