The software described in this guide is furnished under a license agreement and may be used only in accordance with the terms of the agreement.
Information in this document is subject to change without notice. The names of companies, products, people, characters, and/or data mentioned herein are fictitious and are in no way intended to represent any real individual, company, product, or event, unless otherwise noted. Complying with all applicable copyright laws is the responsibility of the user. No part of this document may be reproduced or transmitted in any form or by any means, electronic or mechanical, for any purpose, without the express written permission of WinAbility Software Corporation. WinAbility Software Corporation may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from WinAbility Software Corporation, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property.
NO WARRANTY
The technical information in this document is provided AS-IS and WinAbility Software Corporation makes no warranty as to its accuracy or use. Any use of the information contained herein is at the risk of the user. This document may include technical or other inaccuracies or typographical errors.
Copyright Notice
© 2026 WinAbility Software Corporation. All rights reserved.
Trademarks
WinAbility, WinAbility.Com, USBCrypt, and "The Way Software Should Be!" are either registered trademarks or trademarks of WinAbility Software Corporation and/or its suppliers in the U.S.A. and/or other countries. Other product and company names mentioned in this document may be the trademarks or registered trademarks of their respective owners and are hereby acknowledged.
Thank you for choosing USBCrypt!
USBCrypt™ is a software utility that you can use to encrypt USB and other removable and fixed drives with strong encryption:
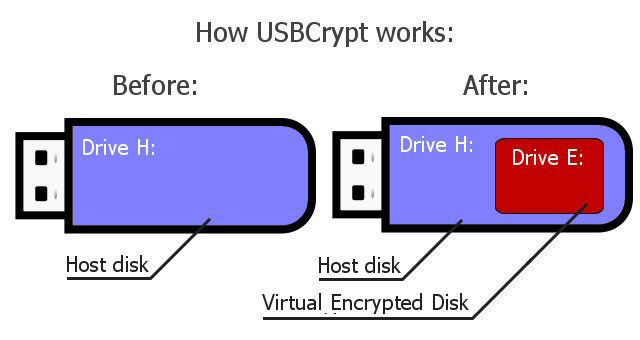
When you encrypt a host disk (such as drive H:) with USBCrypt, it uses a portion of the host disk to create a Virtual Encrypted Disk with its own drive letter (such as drive E:). The drive E: becomes available only after you have entered a valid password. Any file you put onto the drive E: will be encrypted and decrypted on-the-fly, in the background, as necessary.
USBCrypt is the "on-the-fly" encryption software, that works by creating a Virtual Encrypted Disk on the host drive and protecting it with the password of your choosing. You decide how large the Virtual Encrypted Disk should be: it can take all of the available space of the host disk, or only a fraction of it. After you encrypt a drive with USBCrypt, you can enter your password to start the Virtual Encrypted Disk and use it just like any other real disk: you can browse it with Windows Explorer or any other software you have, copy files to it, or move them back to your main hard disk, save documents to the Virtual Encrypted disk and open them when needed, and so on. Any file that you move to the Virtual Encrypted Disk gets encrypted transparently, without you having to do anything special. When you open a document or move a file out of the Virtual Encrypted Disk, it gets decrypted automatically on the fly. When you no longer need to work with the private files, you can stop the Virtual Encrypted Disk and it will become locked with your password again.
USBCrypt puts its software on the encrypted drive, too, to make you able to use the removable drive on other computers, without USBCrypt installed on them. For example, if you've purchased USBCrypt for use in your office, you can take the encrypted USB drive home with you and use it on your home computer without installing the full copy of USBCrypt software on your home computer.
How strong is the encryption of USBCrypt?
USBCrypt uses the Advanced Encryption Standard (AES) ![]() with the key strength of 128 or 256 bits. (Business customers have the option of using several other encryption algorithms, as well). This encryption is very strong: there is currently no realistic method that can break such encryption. Checking all possible keys would take a long, long time
with the key strength of 128 or 256 bits. (Business customers have the option of using several other encryption algorithms, as well). This encryption is very strong: there is currently no realistic method that can break such encryption. Checking all possible keys would take a long, long time ![]() (longer than the age of the Universe). The only way to get access to the files protected with USBCrypt is to provide the correct password. This is the good news; the bad news is that if you forget your password, there would be no way to get your files back. To protect you from such an unpleasant situation, USBCrypt offers you an option to create a spare key file on your computer.
(longer than the age of the Universe). The only way to get access to the files protected with USBCrypt is to provide the correct password. This is the good news; the bad news is that if you forget your password, there would be no way to get your files back. To protect you from such an unpleasant situation, USBCrypt offers you an option to create a spare key file on your computer.
Is administrator access needed to use USBCrypt?
Just like with most other software, the administrator rights are required to install USBCrypt on a computer. The administrator rights are also necessary to create the Virtual Encrypted Disks. If you attach the encrypted drive to another computer that does not have USBCrypt software already installed on it, the administrative rights are needed to use the encrypted drive on such a computer. However, to use the encrypted drives on your own computer(s) where you have already installed USBCrypt software, the administrative rights are NOT required.
Can I encrypt non-USB drives?
Yes! While USBCrypt is designed primarily to encrypt the removable USB disks, it can encrypt other types of disks, as well, including FireWire and the local ones. The general rule is: if you can see the disk as a local or removable drive in the Computer folder, and you can create files on the disk, then you can use USBCrypt to encrypt such a disk.
Can I use the encrypted drive on another computer?
Yes, you can, even if that computer does not have USBCrypt software installed on it, as long as the computer is running a supported version of Windows. Note that you may need to get an administrator approval to use an encrypted drive on another computer.
Any other questions?
Please see the answers to the Frequently Asked Questions.
Version 25.6 (June 10, 2025)
This update corrects a problem that in some situations prevented the Brutal force option from taking effect when stopping a Virtual Encrypted Disk.
Version 25.5 (May 25, 2025)
This update offers several improvements and corrections, such as:
- The Virtual Encrypted Disks created with the NTFS encrypted fle system can now be resized;
- Improved detection of the files in use when stopping a Virtual Encrypted Disk;
- Several other minor improvements and corrections have been made.
Version 23.9 (September 15, 2023)
This update offers several improvements and corrections, such as:
- A problem has been corrected that in some situations caused a delay of several seconds when contacting the license validation server;
- Several elements of the user interface have been repositioned for improved user experience;
- Several other minor improvements and corrections have been made.
Version 22.10 (October 26, 2022)
This update offers several improvements and corrections, such as:
- Improved support for the ARM 64-bit processor architecture;
Version 21.3 (March 20, 2021)
This update offers several improvements and corrections, such as:
- Native support for the ARM 64-bit processor architecture;
- Several other minor improvements and corrections have been made.
Version 21.1 (January 31, 2021)
- Several new options have been added to the USBCrypt Settings screen to allow you to hide the taskbar notification icons or suppress the notification messages displayed by USBCrypt.
- A new command has been added that allows one to convert Virtual Encrypted Disks created with the Encryptability
 software to the USBCrypt format.
software to the USBCrypt format.
- Several other minor improvements have been made.
Version 18.5 (May 30, 2018)
This update adds support for the SHA3 and SHA2 hash algorithms for derivation of the encryption key, in addition to the SHA2 Combo algorithm used in the previous versions of USBCrypt.
Version 16.10 (October 25, 2016)
This update enables the use of USBCrypt on clean installations of Windows 10 build 1607 and Windows Server 2016 with Secure Boot enabled.
Version 16.6 (June 15, 2016)
- The administrator approval is now required not only when creating a new Virtual Encrypted Disk, but also when deleting or updating an existing one.
- A new option has been added, Split the host file into segments.
- Several other minor improvements have been made.
Version 15.8 (August 9, 2015)
- USBCrypt is now officially certified by Microsoft as software compatible with Windows 10.
- Several other minor improvements have been made.
Version 15.4 (April 12, 2015)
This update offers several improvements, such as:
- Full support for the exFAT file system, on those versions of Windows that offer exFAT support.
- A new command, PANIC, has been added to the USBCrypt notification icon menu.
- When creating a new Virtual Encrypted Disk, the name you have chosen for the disk is now used as the drive label of the Virtual Encrypted Disk. Note that if you chose to format the drive with the FAT or exFAT file system, and the name is longer than 11 characters, it will be truncated at 11th character, due to the limitations of the FAT/exFAT file systems.
- A new Group Policy has been added to the Administrator's Kit that enables the administrator to hide the license key information on the About USBCrypt window.
- The look of the main window of USBCrypt has been changed to give the 'flat' appearance.
- Several other minor improvements have been made.
Version 14.6 (June 4, 2014)
This is a maintenance release that includes several improvements and fixes, such as:
- A problem has been corrected that caused Windows to display an error message when using the System Image backup program of Windows even though no Virtual Encrypted Disks have been started.
- Several other minor improvements have been made.
Version 13.11.1 (November 11, 2013)
This is a major upgrade that includes several improvements and fixes, such as:
- A new format for the Virtual Encrypted Disks that allows for encrypting drives as large as 128 TB (tera-bytes).
- An option to skip encrypting the empty space of the drive, that dramatically increases the speed of the initial drive encryption. For example, while the previous version could take several hours to encrypt a large drive, now the same process takes less than a minute!
- When stopping a Virtual Encrypted Disk that is still in use, you can now see which processes still have the files open on that disk, and stop or even terminate them directly.
- If the host disk encounters an error while reading or writing the encrypted data, USBCrypt now notifies you immediately, by displaying a popup "balloon" in the taskbar notification area.
- Many other improvements "under the hood", that make USBCrypt even faster and more reliable than before.
Version 10.9.5 (September 15, 2010)
This is a maintenance release that includes several improvements and fixes, such as:
- In some usage scenarios, the Optimize for performance option could cause 100% of the available RAM to be consumed. We have corrected that.
- When encrypting a drive, the size of the Virtual Encrypted Disk can now be selected using units other than MB.
- The size of the Virtual Encrypted Disk is now displayed when choosing the Properties command from the taskbar icon right-click menu.
Version 10.8.5 (August 30, 2010)
This version includes many improvements and fixes, such as:
- An option to select the preferred optimization of the Virtual Encrypted Disks: you can now choose whether to optimize for performance or for quick removal of the encrypted disks.
- An option to launch the "autorun" process "As Administrator" when starting or stopping the encrypted disks.
- You can now create custom names for the host disks (other than the default USBCrypt Host disk), to make it easier to recognize different disks in the Explorer windows.
- While the encryption process of a drive is in progress, you can now minimize the USBCrypt window to the taskbar. You may find it handy when encrypting large drives.
- Also, you can now pause and resume the encryption process, if you need to temporarily allow other programs to use the full CPU power of your computer.
- The built-in backup software that comes with Windows 7 or Windows Vista can now recognize the Virtual Encrypted Disks as valid backup destinations for the documents and settings.
- USBCrypt now warns you if you log off or shut down the computer while a disk is being encrypted.
- And more! Please give the new USBCrypt a try.
Version 10.3.0 (March 10, 2010)
The first release of USBCrypt: everything is new!
The installation and operation of USBCrypt software is supported on the versions of Windows that are fully supported by Microsoft. At the time of this writing, the supported versions of Windows are:
- Windows 11
- Windows 10
- Windows Server 2025 (with Desktop experience)
- Windows Server 2022 (with Desktop experience)
- Windows Server 2019 (with Desktop experience)
- Windows Server 2016 (with Desktop experience)
Both the 32-bit and x64 editions of Windows (including ARM 64-bit) are supported.
USBCrypt may be able to work on the following older versions of Windows in the test signing mode:
- Windows 8.1
- Windows 7 with Service Pack 1
- Windows Server 2012 (with Desktop experience)
- Windows Server 2012 R2 (with Desktop experience)
Note that Windows Vista x64 and Windows Server 2008 x64 are NOT SUPPORTED. The reason is that Microsoft chose not to update ![]() these versions to support the SHA256 digital signatures in the kernel mode, and without such support such systems cannot use the USBCrypt kernel driver.
these versions to support the SHA256 digital signatures in the kernel mode, and without such support such systems cannot use the USBCrypt kernel driver.
IMPORTANT: For each supported version of Windows, all available service packs and Windows updates must be installed. If your computer is not set to install updates automatically, use Windows Update to check for available updates and install them. USBCrypt may not work properly if the latest updates are not installed.
Note that some features of USBCrypt depend on support from Windows and not all versions and editions of Windows provide such support equally well. You are strongly advised to try the software before purchasing it to verify it's working well enough in your particular software environment.
USBCrypt may work with some of the older versions of Windows, such as Windows XP, Vista, or Windows 7, but we do not support such configurations. You are advised to thoroughly test the software on the unsupported versions of Windows prior to purchasing it, to make sure it operates according to your requirements "out of the box".
USBCrypt is NOT compatible with Windows RT, Windows 95, 98, Me, Windows NT, Windows 2000, or any older version of Windows. USBCrypt is NOT compatible with Linux, OS X, or other operating systems that are not based on Windows.
Both Encryptability ![]() and USBCrypt
and USBCrypt ![]() are encryption products that are used to create and manage Virtual Encrypted Disks. Both of these products allow you to create Virtual Encrypted Disks on both the internal and external storage devices, and access the encrypted files via the virtual drive letters, just like the real drives. They both use the same encryption methods and algorithms, and offer the same strength and protection against unauthorized access to the encrypted files and folders.
are encryption products that are used to create and manage Virtual Encrypted Disks. Both of these products allow you to create Virtual Encrypted Disks on both the internal and external storage devices, and access the encrypted files via the virtual drive letters, just like the real drives. They both use the same encryption methods and algorithms, and offer the same strength and protection against unauthorized access to the encrypted files and folders.
They differ, however, in the ways they handle the Virtual Encrypted Disks: Encryptability was designed to better handle the Virtual Encrypted Disks on the stationary storage, such as non-removable hard drives, while USBCrypt is better suited for handling encryption of the removable drives.
Here are some of the specific differences you may want to consider when deciding which product, USBCrypt or Encryptability to use in each situation.
- When you encrypt a removable drive with USBCrypt, it adds a portable version its own software to the drive, to allow you to use the encrypted drive on the computers that do not have USBCrypt software installed on them. (The administrator approval is still required, though.) Encryptability does not add software to the removable drives, so they could be used only with the computers that already have Encryptability software installed.
- USBCrypt only supports one Virtual Encrypted Disk per each physical host drive, while Encryptability allows you to create any number of Virtual Encrypted Disks on the same physical storage device, as long as you choose to keep them in separate folders.
- When encrypting a removable drive, USBCrypt checks the NTFS permissions of the host drive. If such permissions pevent the use of the drive with other computers, USBCrypt offers to correct the situation, while Encryptability does not check for such a condition.
- Encryptability supports creating Virtual Encrypted Disk hosted on the shared folders located on other computers connected to your network, while USBCrypt does not support encrypting the network drives.
- USBCrypt displays a separate taskbar notification icon for each encrypted drive, while Encryptability displays only one such icon, that combines the menus for all available Virtual Encrypted Disks.
You can use both USBCrypt and Encryptability on the same computer, but keep in mind that each Virtual Encrypted Disk can be controlled by only one product as the same time. (You can convert the Virtual Encrypted Disks from the Encryptability format to USBCrypt and back.)
Or, you can choose only one of the products, USBCrypt or Encryptability, that matches the way you work better. If you are not sure which one to choose, you are welcome to try them before purchasing: each product comes with a built-in license for a free 30-day evaluation use.
- Login to Windows as the administrator, or as a power user. If you login as a regular or limited user, you may not be able to install or use this software.
- To begin the installation, simply run the installation file. If you do not have the installation file, please visit our web site to download the latest version:
https://www.winability.com/download/

- Note that if you have a previous version of this software already installed on your computer, the installation utility may prompt you to restart the computer, in order to be able to replace the files currently in use by Windows.
- The installation program will walk you through the process of setting up USBCrypt. You will be prompted to read and accept the End User License Agreement, and to select the installation options such as the folder where to copy the files.
- After you press the Finish button, the installation program will copy the files into the specified folder and configure Windows for using USBCrypt. If the installation program detects that your version of Windows is 64-bit, it installs the 64-bit files. Otherwise, it installs the 32-bit files.
- IMPORTANT: Make a backup copy of the installation file of USBCrypt that you have downloaded from our web site, as well as a copy of the message with your license key, on a CD-R or other removable disk, because if you ever need to reinstall the software, you will need both, the installation file and your license information to install the program in the fully-licensed mode. It's not enough to store the files on your hard disk, because when (not if) it crashes, you will lose the files. (Yes, hard disks do crash, believe us!) We provide for download from our web site the latest versions of the installation files only. When we release an updated version, we remove the older version from the download area, so the installation file with the version that you have purchased may not be available for download in the future. Remember, it's your responsibility to backup your important files! If you do misplace your license key or the installation file that we no longer offer for download, please use this link to order a replacement:
https://www.winability.com/store/?lost_key

To completely uninstall USBCrypt, it's not enough to simply delete its program files from the installation folder. To completely remove USBCrypt from your computer, follow the instructions below.
IMPORTANT: If your computer is configured for several user accounts, login into the same user account that you were logged in when you were installing USBCrypt. If you use Windows Fast User Switching, log off from all other accounts before trying to uninstall USBCrypt.
The first step is to decrypt the removable drives that you have previously encrypted with USBCrypt. For each such drive: attach it to your computer, start the Virtual Encrypted Disk it contains, and copy all files out of it to your hard drive or another removable drive that is not encrypted with USBCrypt. Then stop the Virtual Encrypted Disk and run USBCrypt off the Start Menu to delete the Virtual Encrypted Disk from this particular host drive. Make sure you have moved all important files out of the Virtual Encrypted Disk before deleting it, because the deletion is irreversible!
Note that if you plan to reinstall USBCrypt later on, you do NOT need to delete the Virtual Encrypted Disks: you should be able to continue using them, as before, after you install USBCrypt back. However, make sure that each such Virtual Encrypted Disk is stopped before uninstalling USBCrypt. If Windows refuses to stop any Virtual Encrypted Disk because it still has files in use, restart the computer to release the files. (Do not start any Virtual Encrypted Disks after restarting Windows.)
After all Virtual Encrypted Disks have been stopped or deleted, go to Windows Control Panel, open the Apps, Programs and Features, or Add/Remove Programs item, and use it to uninstall USBCrypt.
You may also be prompted to restart your computer, in order to deactivate USBCrypt and release its files that are currently in use by Windows, before the removal can be completed.
If you want to install a new version of USBCrypt on a computer that already has an older version of USBCrypt installed, you do not need to uninstall the old version first. What you need to do, though, is stop all Virtual Encrypted Disks currently active on the computer before starting the upgrade. (If you forget to stop such a disk, the installation utility of USBCrypt should remind you about it.)
After you've stopped all Virtual Encrypted Disks, run the installation file with the new version of USBCrypt, and it should replace the old version with the new one (that is, upgrade your version of USBCrypt).
After the USBCrypt software on the computer has been upgraded, you may also want to upgrade the copies of the USBCrypt software on the encrypted host drives, as well: when you attempt to start a Virtual Encrypted Disk, if USBCrypt detects that the host drive contains an older version of the software, it prompts you to update it:
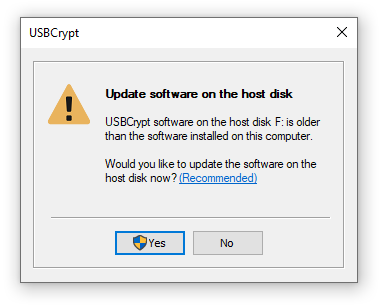
Reply Yes, and USBCrypt will put a new copy of its software on the host disk, bringing it up to date.
USBCrypt is the "try-before-you-buy" software. It means that you can download the fully functional software from our web site and give it a try to see whether it suits your needs and works well enough for you. If it's not up to your expectations or requirements, simply uninstall it from your computer, you have no obligation to continue using the software or pay for it unless you want to. If you do decide to keep the software and continue using it, you can purchase a license for the continued use, enter your license key into the program, and then start using USBCrypt for real, not just for evaluation.
During the evaluation, USBCrypt works in exactly the same way as after you purchase a license for its continued use: there is NO functional difference between the evaluation and the fully licensed versions of this software. We make the evaluation versions this way so you can have a real look at them to decide whether or not they fit your needs.
The only thing different during the evaluation of USBCrypt is that it uses a "weak" password protection of the encrypted data: it allows anyone to recover the "weak" password of a Virtual Encrypted Disk within a few minutes or hours (depending on the computer speed). USBCrypt displays the following message when you set up a new password for Virtual Encrypted Disk during the evaluation period:
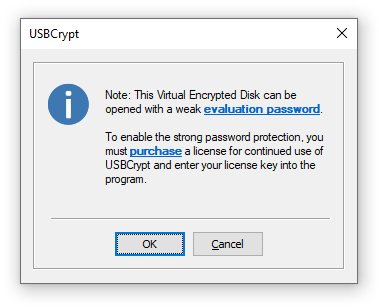
Note that the "weak" password protection does not affect the speed of encryption, or the performance of the file operations on the encrypted volumes, or anything else: USBCrypt operates in exactly the same way, with the same speed. After you purchase a license for continued use of USBCrypt, the next time you start the Virtual Encrypted Disk, it prompts you to remove the "weak" password protection from it:
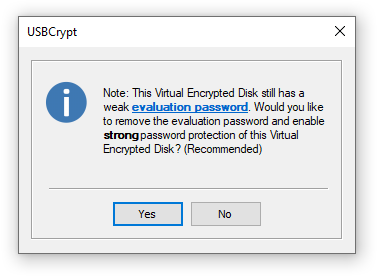
All you need to do is press the Yes button, and USBCrypt will instantly remove the "weak" password protection from the Virtual Encrypted Disk and enable the full, strong password protection.
We accept all major credit cards, and we also offer many other payment options.
Open one of our web sites listed below, click on the Purchase or Buy Now link, and it will take you directly to our secure online store, where you can see the latest pricing and discount information, our money-back guarantee, privacy policy, and other related information:
We provide free software updates to the same product that we may release within one year from the date of your purchase. For example, if you have purchased your license on March 1, 2025, you may use that license key for all updated versions of the same product that we may release during the next year, up to March 1, 2026 (both minor and major updates are covered by this offer). In other words, within one year after the purchase you get all updates to the product free of any charges.
After that, to update to a newer version, you would need to purchase an upgraded license. Please note, you are in no way obligated to update to the new versions: you may continue using the version that you have purchased for as long as you like, if it works for you well enough, without paying any additional upgrade fees.
Please visit our web sites for the latest information:
USBCrypt can check for the updates for you, either manually or automatically:
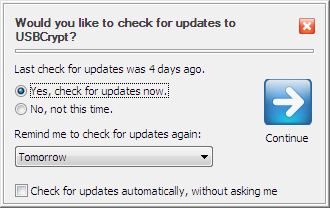
You can choose how often you want USBCrypt to remind you to check for the updates (daily, weekly, monthly, or never). You can also set up USBCrypt to check for the updates automatically, without asking you.
Note that you may need to configure your firewall, anti-virus, and/or anti-spyware software to allow USBCrypt to connect to the Internet, otherwise it may not be able to receive the information about the updates.
Related topics:
We provide free online support to the licensed customers through our web site, for at least one year after the purchase. The prospective customers evaluating the software are welcome to use our support area, too. Before requesting technical or customer support, however, please check out this manual, it may already contain the answer to your question. In particular, be sure to look through the FAQ (Frequently Asked Questions) section of this guide.
Please DO NOT send us email messages, because due to the spam, worms, and spyware problems the reliability of email has diminished greatly in the last few years. The email messages that you send us often do not arrive, and if they do, our replies are often get blocked by your anti-spam or anti-virus software, causing frustration and unnecessary delays in communication.
Please visit our web site to request technical or customer support:
Before you can use your USB drive to keep your private files, first you need to encrypt that USB drive with USBCrypt software. Specifically, you need to use USBCrypt software to create a Virtual Encrypted Disk on your USB drive. After the Virtual Encrypted Disk has been created, you can put your private files into it to keep them strongly encrypted and protected.
To create a Virtual Encrypted Disk, simply run USBCrypt (by using its desktop icon, for example) and select the USB drive that you want to host the Virtual Encrypted Disk from the drop-down list:
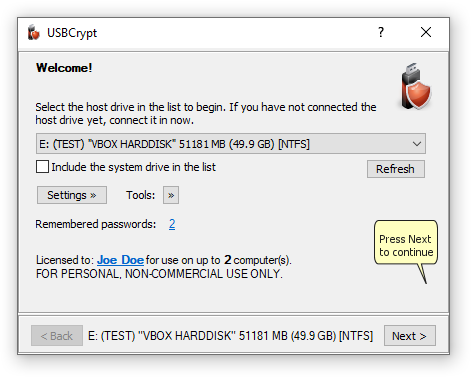
If you have not plugged your removable USB drive into the computer yet, you can plug it in now and it should appear in the list after a few seconds. Or, you can press the Refresh button to update the list of the removable drives manually. Note that by default the system drive (usually the C: drive) is not included in the list; if you want to be able to create a Virtual Encrypted Disk on the system drive, select the Include the system drive in the list option.
When you select a drive in the list, its description appears at the bottom of the USBCrypt window. The description usually includes the drive letter currently assigned to the drive, its label (if any), the name of the manufacturer (as reported by the drive itself), the capacity of the drive and the current file system it's been formatted with.
After you've selected the desired USB drive in the list, press the Next button. USBCrypt will take a moment to analyze the drive you've selected. If it detects that it has not been encrypted yet, it may show the following prompt:
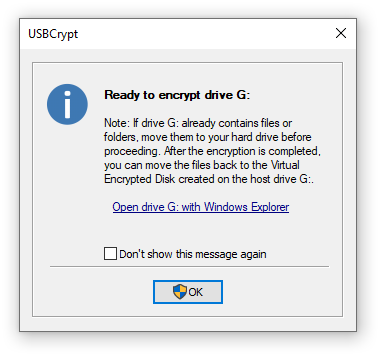
(Note that if you've selected a drive that has already been encrypted with USBCrypt, a different window will be shown). This message serves as a reminder to move any existing files from the host USB drive to the main hard drive of your computer before proceeding with the encryption. The reason is that USBCrypt first needs as much free space on the USB drive as possible to allocate for the Virtual Encrypted Disk. If you have previously put some files on the USB drive that you want to be encrypted, you can take this opportunity and click on the Open drive ... with Windows Explorer link and drag and drop the files from the USB drive to your computer's hard drive (for example, to the Documents folder). Of course, you can use another file manager (such as our AB Commander ![]() ) to move the files, too. If you want to encrypt a fresh USB drive that has no files on it yet, you can just press OK to continue.
) to move the files, too. If you want to encrypt a fresh USB drive that has no files on it yet, you can just press OK to continue.
At this point, USBCrypt should start the encryption wizard that should guide you through the process of encrypting the USB drive. (If you are using the computer as a non-administrator, you will need to provide the administrator credentials to continue.)
Next step: Choose name
The first screen of the wizard prompts you to choose a descriptive name for the Virtual Encrypted Disk you are about to create:
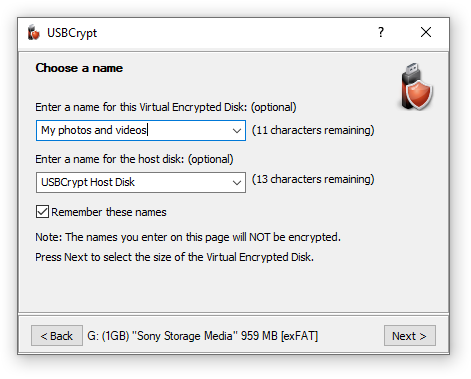
The name of the Virtual Encrypted Disk that you enter here will be displayed by USBCrypt on its windows and menus later on, when you will be working with the encrypted drive. If you plan to encrypt several USB drives, you may want to enter the descriptive text here to help you distinguish between these USB drives later on. For example, if you plan to use the drive mainly to store your vacation photos, you can name it Photos. Keep in mind that this name will NOT be encrypted: it will be shown on the USBCrypt screens even before the correct password is entered. You also have the option of not entering any name at all: if you leave the name box empty, USBCrypt will not be displaying any name on its screens later on.
You also have the option of entering a custom name for the host disk. The host disk name is displayed by Windows when you open the Computer (or My Computer) folder, as a label next to the host disk's icon.
Note that USBCrypt can remember the names that you enter here: if you select the option Remember these names, then next time you run USBCrypt you can see the previously entered names by clicking on the down arrows at the far right end of the Enter a name boxes. You can select one of the previous names in the list to use it without typing the name again. If you don't want the name to be remembered in this way, clear the Remember these names option before clicking on the Next button. You can also choose the Clear all command (the last item on the list of names) to erase the list and make USBCrypt "forget" them.
Next step: Choose size
The next step of the wizard lets you choose the size of the Virtual Encrypted Disk to create:
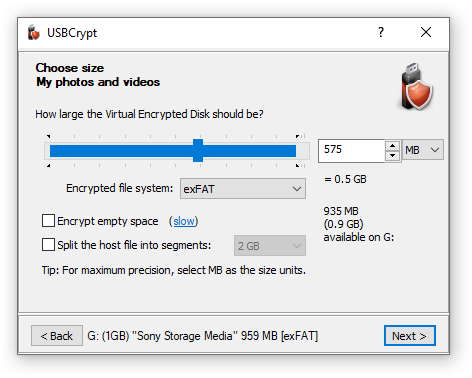
You can use either the slider to choose the portion of the available space to encrypt, or enter the desired size directly into the box to the right. The minimum size is 1 MB, the maximum is only restricted by the available free space on the USB drive and by the limitations of the operating system.
What size you should choose depends on how you are going to use the USB drive: do you want to use it only to store the encrypted files, or do you want to be able to put unencrypted files on it, too? If it's the former, select all allowed space to be used for the Virtual Encrypted Disk. In the latter case, only a portion of the disk to encrypt and leave enough room for the unencrypted files.
The portion of the slider displayed in the blue color indicates the available free space on the host drive. It shows the maximum size of the Virtual Encrypted Disk that can be created on the host disk. If you want a larger portion of the host drive to become available for encryption, you need to move some files out of the host drive, before encrypting it.
Besides the size, this window also lets you choose the file system to create within the Virtual Encrypted Disk by selecting it in the Encrypted file system list. (If you do not make the selection then by default the encrypted file system will be the same as the file system of the host USB drive.) Read more...
Another important option available on this screen is Encrypt empty space. This option greatly affects the speed of creation of the Virtual Encrypted Disk. Read more...
Finally, the option Split the host file into segments offers you more control of how the Virtual Encrypted Disk is stored on the host drive. Normally, you don't need to change this option: it will be automatically selected for the FAT/FAT32 host drives, and deselected for the NTFS and exFAT drives, as needed. If you have a good reason for the host file to be split in segments even on the NTFS or exFAT host drives (an example of such a reason could be if you plan at some point to move the Virtual Encrypted Drive to another host drive, formatted with FAT or FAT32), then you are free to select this option. In such a case, choosing the largest segment size offered (2GB) is preferred, because it would reduce the number of the segments that USBCrypt software would need to keep track of.
If this option is not selected, then USBCrypt uses a single file to store the contents of the Virtual Encrypted Disk. This setting is recommended if the host drive is formatted with the NTFS or exFAT file systems, which allow for virtually unlimited sizes of the files. However, if the host drive is formatted with the FAT or FAT32 systems, such systems cannot store files of 4 GB or larger size. If you create a Virtual Encrypted Disk of 4GB or large size, then the host file must be split in smaller segments (2GB or smaller each). To accommodate for such a situation, this option becomes automatically selected (and you cannot deselect it) if the host drive is formatted with the FAT or FAT32 file system.
Keep in mind that the Virtual Encrypted Disks created with the option Split the host file into segments cannot be resized. If you want to be able to resize a Virtual Encrypted Disk at a later time, keep this option deselected, and also remember to choose the NTFS encrypted file system.
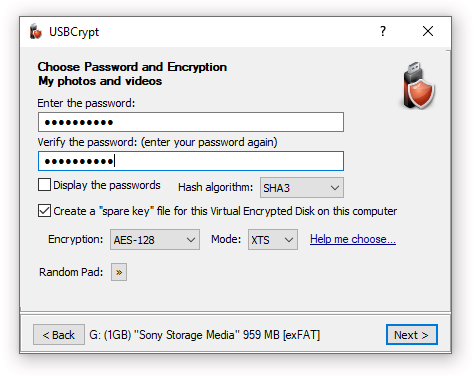
Next step: Choose password and encryption
The next step of the wizard lets you choose a password to protect the Virtual Encrypted Disk:
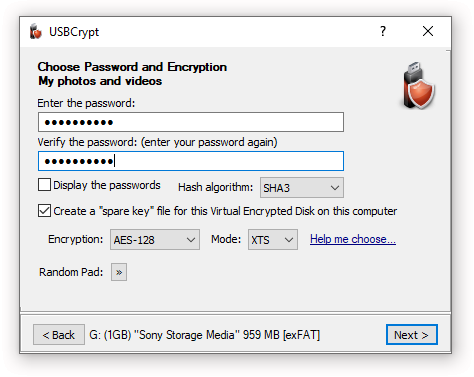
Of course, choosing a good password is tricky. It should be long and complex enough to be hard to guess by others, yet easy enough to remember for you. A strong password should contain a mix of the lower- and -upper-case characters, as well as a few digits and special characters.
Remember that the passwords used by USBCrypt are case-sensitive (that is, Apple, APPLE, and apple are considered different passwords. The maximum number of characters a password may contain is 64.
If you've decided to choose a complex password, you may find the Display password option handy: it lets you see the passwords you are entering in plain view, as they really are. (Just make sure no one is looking over your shoulder before choosing to reveal your password in this way!
Note that if you are still evaluating USBCrypt (that is, you have not purchased a license for its continued use yet), you will see the following warning:

This message reminds you that during the evaluation period USBCrypt is using the "weak" password protection: it allows anyone to recover the "weak" password easily. If you have already purchased a license for the continued use of USBCrypt and entered your license key into the program, then the full, strong password protection will be used and you will not see this message.
Besides choosing the encryption password, you can also select a few related options:
-
Hash algorithm
You can choose the hash algorithm to be used to derive the encryption key
 from your password. The current choices are:
from your password. The current choices are:
- SHA3 - Secure Hash Algorithm 3
 with 512 bits of output. (Supported by USBCrypt v.18 and later.)
with 512 bits of output. (Supported by USBCrypt v.18 and later.) - SHA2 - Secure Hash Algorithm 2
 with 512 bits of output. (Supported by USBCrypt v.18 and later.)
with 512 bits of output. (Supported by USBCrypt v.18 and later.) - SHA2 Combo - a combination of SHA2 and WHIRLPOOL algorithms
 with 512 bits of output. (Supported by USBCrypt v.13 and later.)
with 512 bits of output. (Supported by USBCrypt v.13 and later.)
Each of these choices offers comparable security, so it's up to you which one to choose. Keep in mind though that the SHA3 and SHA2 algorithms are only supported in USBCrypt version 18 and later. If you plan on using a version of USBCrypt earlier than 18, then choose the SHA2 Combo algorithm, which is the only hash algorithm supported by the older versions of USBCrypt.
- SHA3 - Secure Hash Algorithm 3
-
Create a "spare key" file for this Virtual Encrypted Disk on this computer
If you select this option the USBCrypt will create a special file on the hard drive of your computer that it can use later on to reset the password of this specific Virtual Encrypted Disk. You should consider carefully whether you want to use this option or not: it may come very handy if you forget your password, but if someone else can get hold of your files on this computer, they would be able to bypass the password protection and access your encrypted files without knowing your password. If you are worried about the latter, you are perfectly free to clear this option, just remember that in such a case if you forget your password, you will lose your encrypted files forever!
Note that you can use USBCrypt to create or erase the "spare key" file after the Virtual Encrypted Disk has been created. Should you change your mind, you can create or delete the "spare key" file later on.
Note also that each Virtual Encrypted Disk you create requires its own "spare key" file: it's impossible to use one "spare key" file to unlock another Virtual Encrypted Disk. Even if you create exactly the same Virtual Encrypted Disk of the same size and protect it with the same password, you should create a new "spare key" file specifically for it: any other "spare key" file would not work.
-
Encryption and Mode
These options allow you to select the encryption algorithm and encryption mode that should be used for this Virtual Encrypted Disk. AES-128 stands for "Advanced Encryption Standard
 with 128-bit key", and AES-256 selects the same AES algorithm but with the 256-bit key.
with 128-bit key", and AES-256 selects the same AES algorithm but with the 256-bit key. If you have purchased a business license for USBCrypt, you have the option of choosing among several other encryption algorithms: TF-128 stands for Twofish
 algorithm with a 128-bit encryption key, and TF-256 means Twofish encryption with a 256-bit key. Finally, the choice of AES-TF-512 gives you the cascade encryption
algorithm with a 128-bit encryption key, and TF-256 means Twofish encryption with a 256-bit key. Finally, the choice of AES-TF-512 gives you the cascade encryption  algorithm that is a combination of AES-256 and TF-256 with the effective key length of 512 bit.
algorithm that is a combination of AES-256 and TF-256 with the effective key length of 512 bit. The XTS encryption mode
 is considered the best choice at the time of this writing. Business customers can also select the CBC mode
is considered the best choice at the time of this writing. Business customers can also select the CBC mode  which is an older standard that has some deficiencies, but may be required for compliance with some requirements you might have. The default selection of AES-128 and XTS should provide the best encryption method for most situations.
which is an older standard that has some deficiencies, but may be required for compliance with some requirements you might have. The default selection of AES-128 and XTS should provide the best encryption method for most situations. -
Random Pad
This button opens a small pop-up window that you can use to provide USBCrypt with random data by moving the mouse around that window randomly for a few seconds:
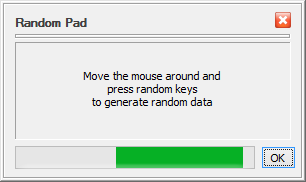
USBCrypt needs random data to generate the encryption keys and related parameters when creating the Virtual Encryption Disk. It collects such random data by monitoring the motion of the mouse and the keystrokes you make while using the previous screens of USBCrypt. Usually it is not necessary to use the Random Pad, because by the time you reach this screen USBCrypt has usually collected enough random data from your use of the previous screens. However, if you want to provide more randomness, you are certainly welcome to use the Random Pad window.
Next step: Formatting the Virtual Encrypted Disk
When USBCrypt is ready to create the Virtual Encrypted Disk, it offers you to review the options that you have selected on the previous screens:
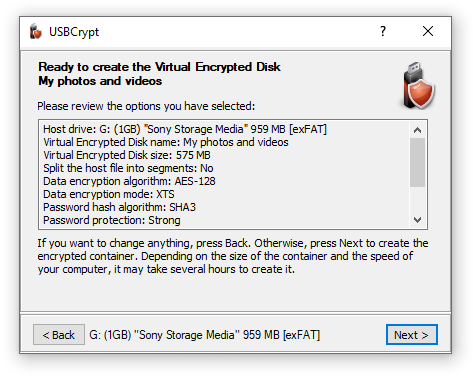
If you want to change anything, it's not too late: simply click the Back button to return to the previous screens and make the changes as desired. If everything looks OK, press the Next button and USBCrypt will start creating a Virtual Encrypted Disk:
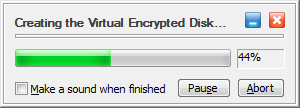
The process may take from a couple of minutes to several hours, depending on the size of the Virtual Encrypted Disk you are creating and the speed of the host drive. For the large or slow drives, you can pause the encryption process and resume it later, if you need to allow some other program to use the full processing power of your computer for a period of time.
Next step: The Virtual Encrypted Disk is ready for use!
After USBCrypt is done creating the Virtual Encrypted Disk, you can start using it right away:
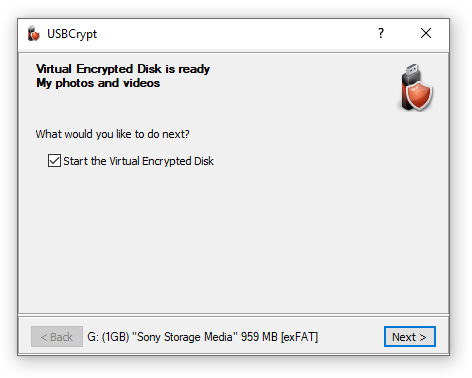
After verifying your password, USBCrypt should start the Virtual Encrypted Disk and assign a drive letter to it, as if you would have attached a real removable disk to the computer:
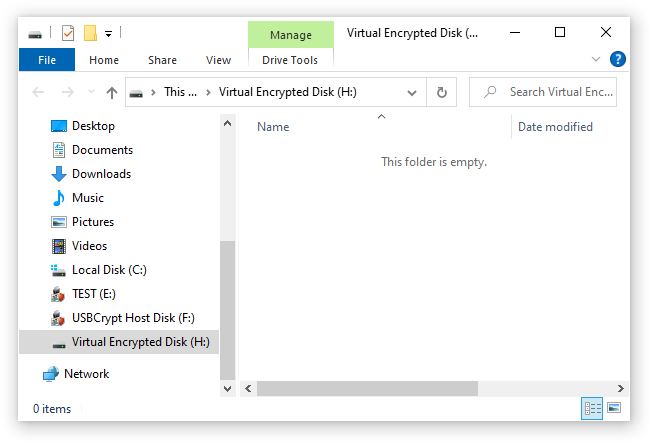 >
>
As you can see, the Virtual Encrypted Disk is initially empty: it contains no files or folders when you create it. You can start moving or copying the files and folders that you want to be encrypted into the Virtual Encrypted Disk, using the usual tools provided by Windows, such as drag-and-drop. You are also free to use any third party file manager (such as our AB Commander ![]() ) to copy the files to the Virtual Encrypted Disk. After that you can work with your encrypted files in the same way as you would with the regular files: you can rename or move them, open or delete them, create new folders or delete the existing ones - all such operations are completely supported by USBCrypt.
) to copy the files to the Virtual Encrypted Disk. After that you can work with your encrypted files in the same way as you would with the regular files: you can rename or move them, open or delete them, create new folders or delete the existing ones - all such operations are completely supported by USBCrypt.
When you are done working with the files inside of the Virtual Encrypted Disk, it's time to make them protected. You do that by stopping the Virtual Encrypted Disk, using any tool offered by USBCrypt: the menu of the USBCrypt taskbar button, or by running USBCrypt from the Start menu and selecting the Stop Virtual Encrypted Disk command.
If you've created the Virtual Encrypted Disk on a removable drive, then after you've stopped it, you can detach the removable drive from the computer using the usual methods offered by Windows.
When you attach the removable host drive encrypted with USBCrypt to your computer, the USBCrypt icon appears on the "system tray" (officially known as the "taskbar notification area"):
![]()
However, simply attaching the host disk to the computer does not make the encrypted files available for use yet: you need to "start" the Virtual Encrypted Disk first. The easiest way of doing that is via the USBCrypt taskbar icon: simply double-click on it, or right-click and then choose the Start Virtual Encrypted Disk command from the menu:
![]()
If there is no USBCrypt icon on the taskbar, there are other ways of "starting" a Virtual Encrypted Disk. If your computer is configured to automatically run programs from the removable drives when they are plugged it, you may see the following prompt displayed by Windows:
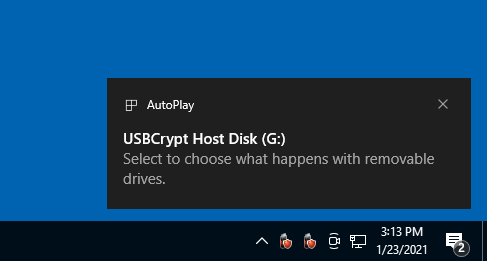
Choose the Open folder to view files command. Or, you can achieve the same result by navigating to the host drive via the Computer (or My Computer) command on Start menu of Windows:
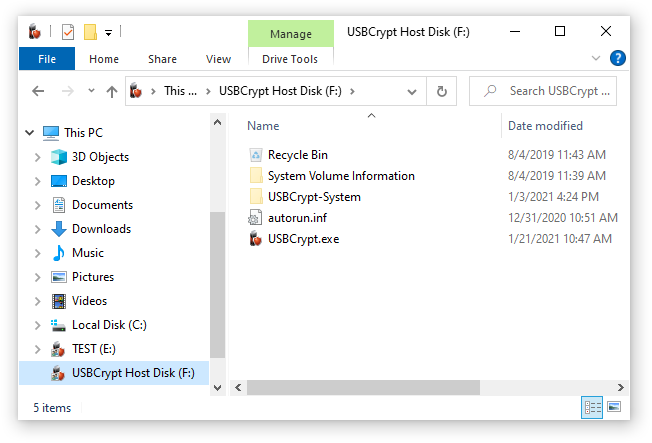
When Windows Explorer window opens, double-click on the USBCrypt.exe file to start USBCrypt software. (You may also see just USBCrypt instead of USBCrypt.exe; if so, double-click on USBCrypt). Also, you may notice a folder named USBCrypt-system there, too: this is a special folder used by USBCrypt to store the files it needs to operate. (Usually this folder is hidden, but your computer may be configured to display the hidden files and folders.) DO NOT go there! OK, I knew it, if told not to do something, it becomes irresistible and now you just have to open that folder, right? OK, go ahead, open it and see what's inside. Nothing interesting, you see? Told you so. Now, close that folder, and don't go there again. OK, if one peek inside was not enough, peek again, but for your own sake, do not delete or rename or do anything else there, because if you do you will void your warranty, lose your encrypted data, and have the eternal curse bestowed upon your entire family. I'm serious. You've been warned. Now get out of the USBCrypt-system folder and never look back.
OK, where were we? USBCrypt should now prompt you to enter your password to start the Virtual Encrypted Disk:
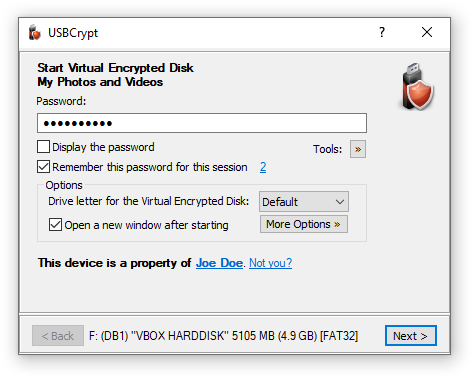
This is the point where those in the know are separated from the rest of the crowd. If you know the password, you will be let in: the Virtual Encrypted Disk will be started and all files and folders it contains will become available for use. If you don't know the password, the Virtual Encrypted Disk will remain the cold pile of useless 1s and 0s and no power in the whole Universe will be able to decrypt them.
Be sure to enter the password exactly as you've supplied it when creating the Virtual Encrypted Disk: the password is case-sensitive, and if you've entered any spaces or special characters when creating the Virtual Encrypted Disk, you need to enter them here as well, in the exact same order. If your computer has several input languages installed, you need to select the correct one, too, by pressing the input language switch key combination defined in Windows Control Panel. You can see the currently selected input language to the right of the password box.
If you are not sure what you've typed in, you can click on the Display the password box and the plain text of the password you've typed in will be displayed in the box. (Before you do that, you may want to check your room for hidden cameras watching your screen. Yes, the bad guys eager to get your secrets could be very sneaky!)
Remember this password for this session option
After you have entered the password and before you press the Next button, take a moment to think about the near future: do you plan to disconnect and then attach the same encrypted drive again, before you shut down the computer? Or, do you have another USB drive encrypted with the same password that you plan to start soon, too? If so, you can save yourself a bit of typing and check the box that reads Remember this password for this session. If you check this option then USBCrypt will remember the password you've just entered until your computer is restarted. This ways, if you attach another encrypted drive, you would not need to enter the same password again: when the password prompt for the second drive appears, you can just leave the password box empty and press the Next button. In such a case, USBCrypt would try the passwords that you have chosen to remember and try them to start the second Virtual Encrypted Disk, without you having to enter the same password again.
If you use the Remember this password for this session option, the password will be remembered until you restart Windows, or choose the Forget passwords command, available on the main USBCrypt screen (by clicking on the number that shows the current number the passwords that USBCrypt keeps in the memory. This command is also available on the menu of the USBCrypt taskbar icon, for quick access when you need it.
(In case you are wondering: USBCrypt does not store the plain text of the password, it only stores its hash value. This way, if someone gets hold of your computer and scans its memory looking for the stored passwords, s/he won't find any.)
Other options
Note also a few more options on the same window that you can select before pressing the Next button. These options let you control what happens after the Virtual Encrypted Disk is started:
Drive letter for the Virtual Encrypted Disk
This option lets you choose the drive letter to be assigned to the Virtual Encrypted Disk after it's started. If you select Default, then the next available drive letter will be used. If you want some other specific drive letter to be used, select it in the list.
Open a new Explorer window
If you select this option, then USBCrypt will open a new Explorer window to display the contents of the Virtual Encrypted Disk.
More Options
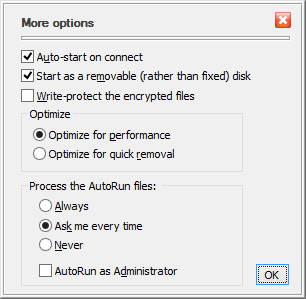
You can click this button to open a list of several additional options:
-
Auto-start on connect
If this option is on, then USBCrypt will automatically display the password entry window when you connect the removable drive to your computer, or when you log in to Windows while the drive is already connected. If this option is off, then you will need to use some other method (like the Start Virtual Encrypted Disk command on the menu of the taskbar icon) to start the Virtual Encrypted Disk off the host drive after you've connected it. Note that this option has effect only if your computer has the USBCrypt software is installed. If you connect the removable disk to some other computer (without USBCrypt software on it), this option has no effect.
-
Start as a removable (rather than fixed) disk
When it comes to the auto-play functionality, the Recycle Bin, optimizations, etc., Windows treats the fixed disks slightly differently than the removable ones. If you require the Virtual Encrypted Disk to be treated as a removable disk, select this option.
-
Write-protect the encrypted files
If you want to protect the contents of the Virtual Encrypted Disk from the accidental (or intentional) changes, select this option: you will still be able to open the files off it and read them but it won't save any changes you make nor will it let you create or delete files or folders on the Virtual Encrypted Disk.
-
Optimize for performance
This option allows Windows to use its file cache mechanism when reading from and writing to the Virtual Encrypted Disk. (No, this does not pose a security risk because the cache is used only for the already encrypted data.) This option offers the best possible performance for the Virtual Encrypted Disk. However, it increases the risk of data loss or data corruption, should your computer lose power or crash at a very unfortunate moment.
-
Optimize for quick removal
If you often encounter the situation that you cannot stop the Virtual Encrypted Disk because it's in use by Windows, you may want to select this option. Note however, that it may slow down the data transfer between the Virtual Encrypted Disk and the rest of the system.
-
Process the AutoRun files
You can use this option to control the automatic execution of the AutoRun file off this Virtual Encrypted Disk on this computer.
-
Of course, you can also leave the options as they are for now, and just enter the password and click Next. What happens then is very much like sort of a digital magic: the random bytes of the Virtual Encrypted Disk that previously were not making sense, are suddenly starting to come together in an orderly way, and the Virtual Encrypted Disk "starts" to come alive: it appears like a regular disk in the Computer folder:

If this is the first time that you've started the Virtual Encrypted Disk, it will be empty. You can start filling it up with the files and folders that you want to be encrypted.
You can see why this disk is called "virtual": there is no actual physical disk with that letter attached to you computer. The C: disk is the main hard drive, the D: disk is your CD-ROM drive, you may or may not have other disks (such as the E: and F: disks shown in the example above). The G: disk is the host USB drive (encrypted with USBCrypt). And, finally, the H: drive, is the virtual disk that appears just like any other disk you might have, but that represents the encrypted area that you have created on the host disk G:.
You can use the Virtual Encrypted Disk just like any real disk: you can create folders inside of it, rename and delete files, change their attributes, open files off it, and so on. You can even defragment the Virtual Encrypted Drive, or share it on your network, if you want. For most practical purposes, the Virtual Encrypted Disk is indistinguishable from any regular disk of the same kind. The only (and very important) difference is that the Virtual Encrypted Disk becomes a disk only after you have entered the correct password. This is something that the regular disks are incapable of.
Go ahead, move your personal files that you want to be encrypted into the Virtual Encrypted Disk that you've just started. If you are only starting learning USBCrypt, you may want not to move, but copy the files for now: in this case, if something goes wrong, and you want to start over, you would still have the original unencrypted copies left on your hard disk. When you are comfortable with the USBCrypt software and the whole concept of the Virtual Encrypted Disks, and also when you have a reliable backup, you can "securely" delete the original unencrypted copies of the private files, and have only the encrypted ones to work with, inside of the Virtual Encrypted Disk.
Now that you've had the Virtual Encrypted Disk started and running, what do you do to lock its back and make the encrypted files protected and inaccessible to no one besides you? For that, you need to stop the Virtual Encrypted Disk and return it to the cold conglomerate of the random 1s and 0s.
When you are done working with the encrypted files located inside of the Virtual Encrypted Disk, you need to stop the Virtual Encrypted Disk, that is, return it into the state in which its contents is inaccessible to anyone who does not know your password.
USBCrypt offers several methods of stopping the Virtual Encrypted Disks. The fastest one is via the system tray icon:
![]()
When you right-click on the icon, a menu is displayed that contains a few commands, one of which is "Stop Virtual Encrypted Disk". When you choose this command, USBCrypt attempts to stop the Virtual Encrypted Disk. It usually takes just a second or two, and if there are no files in use that are located in the Virtual Encrypted Disk, it stops and you can see the result in the "balloon" message above the USBCrypt icon:
![]()
However, if some file is still in use, you may see the following message instead:
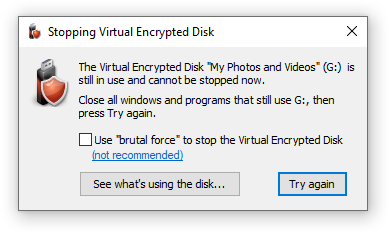
If you see this message, the first thing to try is to do what it tells: close any program that might still be using files off the Virtual Encrypted Disk, including any Explorer windows that might be displaying the contents of the Virtual Encrypted Disk, then press Try again.
If you are not sure which programs are still using the Virtual Encrypted Disk, press the Show what's using the disk button and it should open a popup listing the processes that still have files open on the encrypted disk, such as this:
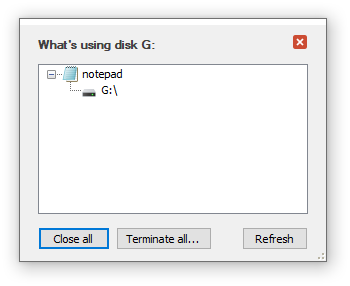
You can use this information to close the listed applications, as you normally do, usually by closing their windows. If for some reason the application does not close normally, you can right-click on each process and choose to close or terminate it. Or, press the Close all button to make USBCrypt to try to close all listed processes. If some of them refuse to close, you can choose to Terminate them instead. However, use these tools only as the last resort, as they can result in a system instability. The preferred way is to close each application normally.
After closing the listed processes, press the Try again button to try to stop the Virtual Encrypted Disk again. If the same message reappears, it might be that some system process or a hidden window is still using a file on the Virtual Encrypted Disk. If you are sure there are no windows or programs that you can close to remedy the situation, there are two courses of action you can take:
The safest method is to restart your computer. (Note that putting the computer to sleep and then waking it up may not work, a complete restart may be required). When the computer shuts down, any Virtual Encrypted Disk that might be running before stops unconditionally. When you power up your computer again, the Virtual Encrypted Disk remain stopped, until you start it again by entering the correct password.
If you are in a hurry and don't want to wait for the computer to restart, you can try the brutal force option shown on the screen above. However, this option should be used only if you are sure there are no open files with unsaved changes. If some file happens to have unsaved changes to it, the unsaved changes may be lost when you stop the Virtual Encrypted Disk "brutally".
In any case, after you stop the Virtual Encrypted Disk (normally or "brutally") its contents becomes locked back. All files and folders that the Virtual Encrypted Disk contains at that point become encrypted and completely inaccessible to anyone. The only way to get access to the files stored inside on a virtual Encrypted Disk is to start it again, by entering the correct password.
After the Virtual Encrypted Disk has stopped, you can eject the host disk from the computer, if you want, using the standard Safely Remove Hardware and Eject Media icon in the system tray:
![]()
If the host drive is removable, you can also use the Stop and eject command on the right-click menu, to achieve the same effect:
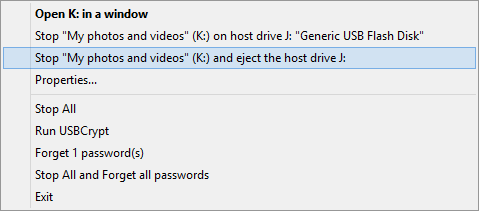
After the drive is ejected, the encrypted files that it contains are stored safely, away from the reach by anyone without the correct password. If you lose the drive, or give it to someone, all the files and folder you've previously put inside of the Virtual Encrypted Disk on it will remain safe.
That describes the typical cycle of the use of an encrypted USB drive: when you need to use the encrypted files, you start the Virtual Encrypted Disk it contains. When you are done working with the files, you stop the Virtual Encrypted Disk.
You have probably noticed that after you've created your first Virtual Encrypted Disk, USBCrypt put a small icon on the system tray (also known officially as the "taskbar notification area") for it:
![]()
When you eject the removable host drive, the icon disappears, and when you plug the host drive back, the icon re-appears on the system tray again. If you plug in another removable drive with a different Virtual Encrypted Disk on it, USBCrypt will show a separate icon for that drive, too. As you can see, the system tray icons give you a quick visual cue about the drives encrypted with USBCrypt that are currently attached to the computer.
If you don't see this icon, it could be because your computer is configured not to display all icons available. To make it display the USBCrypt icon, right-click on an empty area of the taskbar, choose Taskbar settings from the menu, and then click on the link in the Notification area that reads Select which icons appear on the taskbar. (Theis procedure may be different in your version of Windows).
If you click (or right-click) on such an icon, a shortcut menu appears with commands that depend on the current state of the encrypted drive represented by that icon. If you have not started the Virtual Encrypted Disk off it yet, the menu contains a command to start it:
![]()
You can use this command to quickly start the Virtual Encrypted disk. It would have the same effect as if you would have run USBCrypt off the Start menu and then selected the host disk to start in the main list. The system tray icon gives a quicker access to that command.
Notice that when you start the Virtual Encrypted Disk, the system tray icon changes its color from red to green. That provides you with another useful visual cue, especially if you have several USBCrypt drives attached to the computer at the same time: by glancing over the system tray icons you can instantly see which encrypted disks are started and which are not.
If you click on the system tray icon for the Virtual Encrypted Disk that's already started, you would see a slightly different shortcut menu:
![]()
As you can see, this menu gives you a quick access to the command to stop the Virtual Encrypted Disk represented by that icon. Again, the net result is the same as if you would have run USBCrypt main application and chosen the host disk to stop from the list.
The shortcut menu may contains several other commands that you may find useful:
-
Start All
This command appears on the menu if you have several encrypted drives connected to the computer at the same time. This command gives you a quick way to start all Virtual Encrypted Disks from such drives at once, without having to choose the Start command for each encrypted drive individually.
-
Stop All
This command appears on the menu if you have started several Virtual Encrypted Disks. When you choose this command, USBCrypt attempts to stop all active Virtual Encrypted disks. Note that if a Virtual Encrypted Disk cannot be stopped because, for example, it still has open files, USBCrypt displays a notification about such a situation and waits for your response before actually stopping it.
-
Open USBCrypt
This command has the same effect as opening the USBCrypt application using its Desktop icon or Windows Start menu.
-
Forget ... password(s)
This command appears on the menu only if you have previously used the Remember this password for this session command when starting a Virtual Encrypted Disk. You may want to use this command if you no longer want USBCrypt to remember such passwords.
-
Stop All and Forget all password(s)
This command appears on the menu if you have previously started one or more Virtual Encrypted Disks or if you have previously used the Remember this password for this session command when starting a Virtual Encrypted Disk. When you choose this command, USBCrypt attempts to stop all active Virtual Encrypted disks and also erases the previously remembered password hashes from the password hash cache. Note that if a Virtual Encrypted Disk cannot be stopped because, for example, it still has open files, USBCrypt displays a notification about such a situation and waits for your response before actually stopping it.
-
PANIC
This command appears on the menu if you have previously started one or more Virtual Encrypted Disks or if you have previously used the Remember this password for this session command when starting a Virtual Encrypted Disk. This command has the same effect as the Stop All and Forget all password(s) described above, except that if a Virtual Encrypted Disk cannot be stopped because, for example, it still has open files, USBCrypt unconditionally ("brutally") stops such a disk without displaying a notification and waiting for your response.
-
Exit
This command appears only when you use the encrypted drive on a computer without USBCrypt software installed on it. In such a case, the system tray icon is loaded directly from the removable drive itself. If you decide to unplug the drive, Windows won't let you do that, because it would still be using the USBCrypt files off that drive to display the icon. To be able to eject the drive, you would need to use the Exit command first.
If for some reason you don't want the USBCrypt icon to appear on the taskbar, you can hide it using the Windows Taskbar Settings screen, or by deselecting the appropriate option on the USBCrypt Settings screen.
If you've encrypted a drive with USBCrypt and later decided that you no longer want the drive to be encrypted, it's easy to remove the encryption. First thing to do, however, is to start the Virtual Encrypted Disk you want to delete, and make sure it contains no important files. If there are any files that you want to keep, copy them to some other location, onto the main hard drive, or another encrypted disk, because after you've removed the encryption for this particular disk, all previously encrypted files it contained will be removed as well!
Having moved all important files out of the Virtual Encrypted Disk, stop it, then run USBCrypt off the Start menu or desktop, and select the host disk that you want to decrypt:

The next window displayed by USBCrypt allows you to either start the encrypted drive, or delete it:
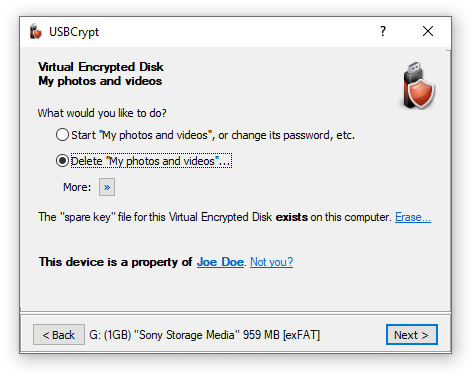
To decrypt the drive, select the Delete option. You will be prompted to confirm your choice and also choose whether you also want to delete the "spare key" file associated with this encrypted disk:
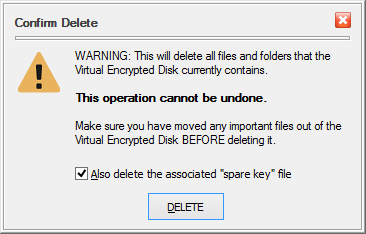
(The option to delete the "spare key" file is available only if USBCrypt can find the "spare key" file on this computer.)
Be sure to review this message and take a moment to consider what it tells you: all files and folders that you have previously moved into the Virtual Encrypted Disk will be deleted. Make sure that you have moved all files and folders that you may need later on out of the Virtual Encrypted Disk (by canceling this prompt and then starting the Virtual Encrypted Disk) before confirming that you want to delete it. If you confirm that you do want to delete the Virtual Encrypted Disk and press the DELETE button, all contents of the Virtual Encrypted Disk will be instantly erased. As the message tells you, there is no undo operation for this action, so think twice before using it.
After you have deleted the Virtual Encrypted Disk, all space it used to occupy on the host drive becomes immediately available for use to store the regular files and folders, as usual, without encrypting them. Or, you can start over and create a new Virtual Encrypted Disk on the same host drive, if that's what you want.
When you run USBCrypt using its Desktop icon or Start menu, you can see that its main window contains the Settings button:

You can press the Settings button to open the USBCrypt Settings window:
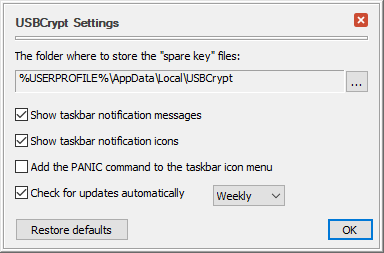
This window contains the following areas:
The folder where to store the "spare key" files
This is the folder on your computer where USBCrypt stores the "spare key" files. (And also where USBCrypt is looking for the "spare key" files when you want to reset a password). You can open this folder to examine its contents or move the "spare key" files to a different folder by clicking on the button to the right of the folder area and using the commands on the menu that opens.
Show taskbar notification messages
If this option is selected, it allows USBCrypt to display notification messages in the bottom right part of the screen) when a Virtual Encrypted Disk has been started or stopped, and in some other cases. You may want to clear this option if you find such messages unnecessary or distracting.
Show taskbar notification icon
If this option is selected, USBCrypt adds its notification icons to the Windows taskbar notification area (next to the system clock, in the bottom right corner of the screen). You may want to clear this option if you prefer not to see the icons and want to leave more room for other icons in the notification area.
Add the PANIC command to the taskbar icon menu
If this option is selected, USBCrypt adds the PANIC command to its notification icon menu that you can use to quickly stop any Virtual Encrypted Disks and "forget" any passwords you've previously chosen to remember. However, since using the PANIC command may potentially cause the loss of the unsaved information, you may want to clear this option to protect yourself from accidentally invoking the PANIC command.
Check for updates automatically
If checked, this option causes USBCrypt to periodically connect to our web site to check for the availability of a newer version. If this option is not selected, then USBCrypt will display a message reminding you to check for the updates manually.
Restore defaults
Press this button if you want to restore the options shown on this screen to their default settings, as they were right after you've installed USBCrypt.
In addition to using the Options window, you can also press the Tools button to display a menu of several commands:
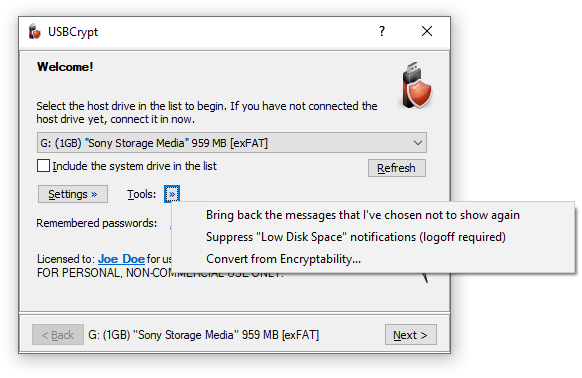
Bring back the messages that I've chosen not to show again
Choose this command to restore the USBCrypt messages that you have previously chosen not to show again.
Suppress/Restore "Low Disk Space" notifications
Choose this command to suppress or restore the notification messages displayed by Windows when the free space on the drives becomes relatively low. You may see such notifications after you have created a Virtual Encrypted Disk to occupy the whole space of host disk. In such a situation, the host disk would have very little unencrypted space left on it, causing Windows to display the "Low Disk Space" notifications. You can use this command to suppress (or restore back) such notifications, Note that if you use this command, you need to log off Windows and then log back on for the change to take effect. Note also that this command affects all drives, not just the ones encrypted with USBCrypt.
Convert from Encryptability...
Use this command to convert a Virtual Encrypted Disk created with Encryptability software into the format used by USBCrypt. After a Virtual Encrypted Disk has been converted, you can use USBCrypt to start, stop, or manage it.
When you were encrypting a drive for the first time, you were prompted to choose both the name for the Virtual Encrypted Disk and also for the host disk:

The name of the Virtual Encrypted Disk is displayed on the USBCrypt screens, in the top part of the windows, for example when starting the Virtual Encrypted Disk:
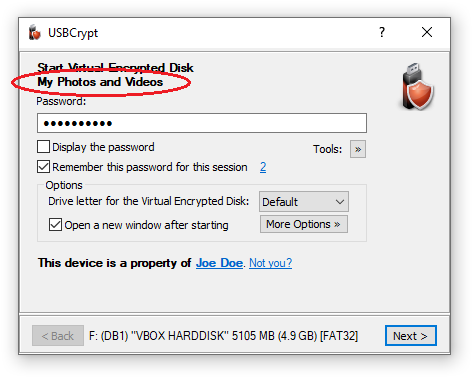
The name of the host disk is displayed in the This PC (or My Computer) folder, as a label next to the disk's icon.
What if later on you've decided that another name would describe your Virtual Encrypted Disk or the host disk better?
No problem, it's easy to rename both the Virtual Encrypted Disk and the host disk. You can do that from the same screen that asks you to start the Virtual Encrypted Disk. Before (or even instead of) entering your password, click on the Tools button, to display a menu with the additional commands:
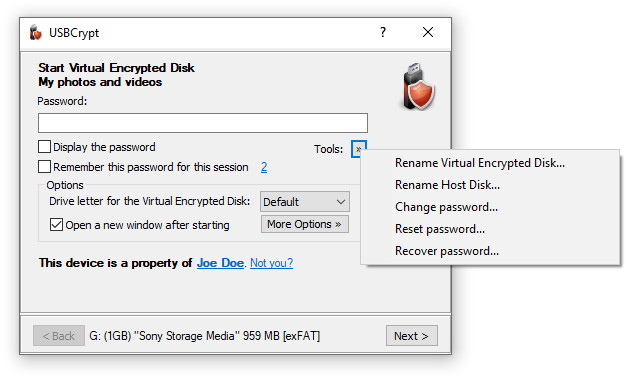
Choose Rename Virtual Encrypted Disk or Rename Host Disk from that menu. You will be prompted to enter a new name. Go ahead, provide the new name (which can be empty, if you want to remove the existing name!) and press Rename:
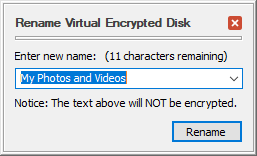
That's all. (That was easy, wasn't it?) If you've renamed the Virtual Encrypted Disk, you should see the new name displayed on the screen immediately. If you've renamed the host disk, then you may need to restart the computer before Windows recognizes the new name.
You can rename a Virtual Encrypted Disk any time you want, as long as the disk has not started yet. If you want to rename a Virtual Encrypted Disk that's already started, you need to stop it first, then use the above procedure to rename it, and after that you can start it again. As for renaming the host disk, you can do it at any time, it does not atter whether the Virtual Encrypted Disk it hosts has already started or not.
If you want to change the password of a Virtual Encrypted Disk, use the same command as if to start the Virtual Encrypted Disk to display the password prompt, but before (or instead of) entering the existing password, click on the Tools button:

Choose the Change password command from the menu, and USBCrypt will prompt you to enter the old password first. If you have entered the old password correctly, it will prompt you to enter a new password:
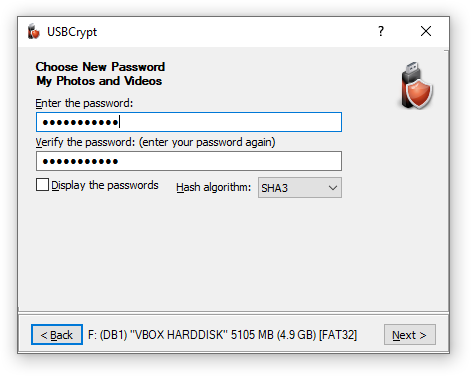
After you've entered the new password (twice), USBCrypt will replace the old password of the Virtual Encrypted Disk with the new password that you have just set up. After that, you should be able to start the Virtual Encrypted Disk by entering the new password (the old password will no longer work).
If you forget the password for a Virtual Encrypted Disk, you may have the option to reset the password. You can access this command by clicking on the Tools command on the password-prompt screen:

If you choose the Reset password command, USBCrypt will try to locate the "spare key" file for this specific Virtual Encrypted Disk, in the folder that is specified in the Options for USBCrypt window. If USBCrypt is able to find the "spare key" file, it prompts you to enter a new password:
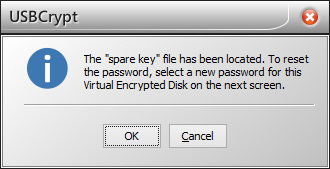
If you press OK and enter a new password on the next screen, USBCrypt will replace whatever the old password of the Virtual Encrypted Disk had before with the new password that you have just set up. After that, you should be able to open the Virtual Encrypted Disk as usual, by entering the new password.
Of course, in order to be able to use the "spare key" file, it must have been previously created by you, for example, by selecting the Create a "spare key" file option when creating the Virtual Encrypted Disk:

The option to create a "spare key" file can be very handy when you no longer remember your real password. However, keep in mind that just as you can use it, anyone else who can get into your computer can use it, too! If your adversaries are smart (and you should always assume that, even if in reality it's not so), all they need to do is have physical access to your computer to be able to reset the password and start your encrypted drive whether you agree to that or not. Don't assume that if your computer prompts to enter the login password, you are protected from your adversaries, no! There are methods of getting to the files stored on your computer without knowing the login password, and if your adversaries want to get to your files badly enough, they will discover such methods, make no mistake about that.
As you can see, the "spare key" option has both the positive and negative consequences, and you should weight the benefits against the risks carefully when deciding whether to use that option or not. Let's summarize:
Benefit: The "spare key" option lets you gain access to your Virtual Encrypted Disk in the event that you forget the real password.
Risk: Anyone who has physical access to your computer can use the "spare key" option to access your Virtual Encrypted Disk without your permission.
Should you NOT use the "spare key" option when encrypting the drives? Such a decision has the benefits and risks, too:
Benefit: Without the "spare key" option no one can peek inside of your Virtual Encrypted Disk. Everyone must provide the real password that you've set up to start the Virtual Encrypted Disk, no exceptions.
Risk: If you forget the password, you won't be able to start the Virtual Encrypted Disk (unless you've selected a very week password that could be recovered in a reasonable time).
So, what should you decide, to use the "spare key" option or not to use it? It's ultimately your decision. Here is some more information about this option to help you decide:
The "spare key" file can be used to reset the password only for that specific Virtual Encrypted Disk for which it was created. You cannot use a "spare key" file to reset passwords of other Virtual Encrypted Disks, even if they have the same real passwords. Even if you delete a Virtual Encrypted Disk and then create exactly the same one again, with the same password and the same size, etc., the original "spare key" file cannot be used to reset the password of the newly created Virtual Encrypted Disk. In other words, the "spare key" option must be enabled or cleared for each Virtual Encrypted Disk individually, and it has no effect on other Virtual Encrypted Disks you might have.
The "spare key" files are stored on your local hard disk, under the Application Data folder (unless you have selected a different folder for that). They are not stored on the removable drives where the Virtual Encrypted Disks are located, or in any other place. It means that if your primary hard disk fails or becomes unusable for some other reason, all "spare key" file would go with it, too. Even if you replace your hard drive with another one of the same size and model, that would not replace the "spare key" files that were on the original hard drive. UNLESS you have specifically taken the steps to backup your original hard drive and then restore it to the new drive.
If you have not chosen the option to create a "spare key" file when creating the Virtual Encrypted Disk, and later changed your mind, you can force USBCrypt to create the "spare key" file later on, by running USBCrypt off the Start menu, selecting the host USB drive in the main list, and then clicking on the Create link in the bottom portion of the screen:
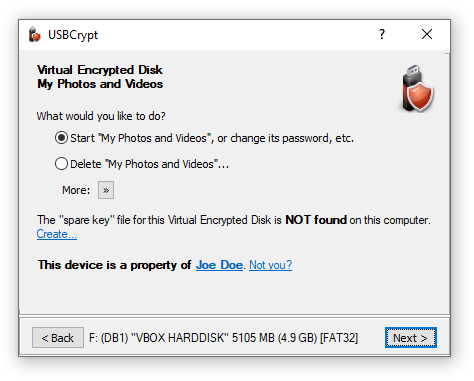
Conversely, if you have chosen to create a "spare key" file when encrypting the drive and later decided you better not have the "spare key" file on your hard drive after all, you can erase it by following the same steps, only this time click on the Erase link instead:
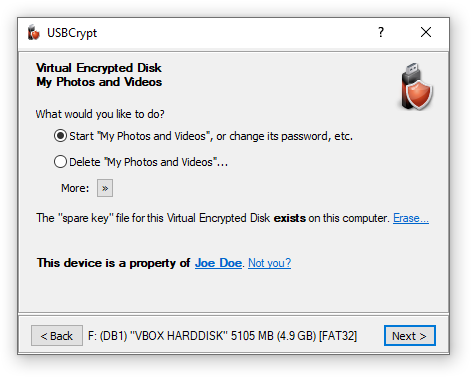
You will be prompted to enter the current password for the Virtual Encrypted Disk, to make sure you don't accidentally erase a "spare key" file for the drive you no longer remember the password of. If you've entered the correct password, USBCrypt will erase the "spare key" file.
IMPORTANT: The "spare key" file is erased with a multi-pass secure erase algorithm that leaves no chance of recovery of this file. Make sure you understand the risks of not having a "spare key" file before you decide to erase it!
Previously we've discussed the "spare key" option that could be of help if you forget the password for an encrypted disk of yours. However, what if you did not select the option to create a "spare key" the on your computer, or if you have replaced your computer at some point and the original "spare key" file is no longer available? Here comes the last resort, the command to recover the lost password, by trying all possible passwords from a specific set of characters, one at a time, until the one of them happens to match the original password.
To get to the password recovery command, start as usual, by running USBCrypt and getting to the point where the password prompted appears in order to start the Virtual Encrypted Disk. Click on the Tools button, and the menu will be shown with the Recover Password command on it:

If you choose the Recover Password command, you will be presented with the following window that asks you to specify the kind of passwords you want to try:
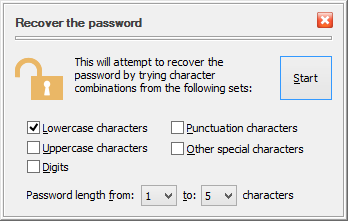
You can specify the minimum and maximum lengths of the passwords, as well the character sets to use when trying the passwords. For example, if choose only the lowercase characters, the minimum lengths 1, and the maximum length 3, then USBCrypt will start applying the 1-character lowercase passwords: a, b, c, and so on, down to z. Each such password would be tested against the current Virtual Encrypted Disk. After all 1-character passwords have been tried, USBCrypt will begin to try the 2-character ones: aa, ab, ac, and so on, down to zz. If none of them unlocks the Virtual Encrypted Disk, it will then try all possible 3-character passwords, until one of them is detected to be able to unlock the Virtual Encrypted Disk (if any).
If you try the Recover password command, you will see that trying each possible password combination in turn takes some time, depending on the speed of your computer. USBCrypt estimates the time that is necessary to try all possible passwords from the set you've defined and displays that estimate on the progress window for you:
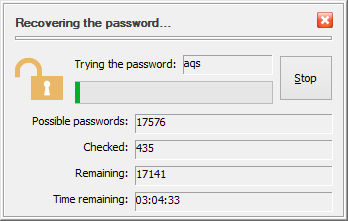
Of course, the estimate depends on the processor speed of your computer. Try it and see for yourself. That could be a good illustration fn the importance of choosing the strong passwords. For example, the amount of time to try all possible 3-character lowercase passwords on a 2GHz dual-core processor is about 2 hours. If you recall that that's exactly how the evaluation passwords are imitated, you will see that if you use USBCrypt in the evaluation mode, anyone should be able to start your Virtual Encrypted Disk by running the recovery password procedure for a mere couple of hours.
If you have purchased a license for continued use of USBCrypt, then the evaluation passwords are not created for your encrypted drives and the strength of the protection is determined exclusively by the complexity of the passwords that you've chosen. For example, on the same processor, to try all possible 5-character passwords that may contain both the lowercase and the uppercase characters as well as digits and special characters, it would take about 30 years to actually try them all. Someone must want to get to your encrypted files badly enough to wait that long! Of course, if someone wants to know your secrets that bad, she could purchase 30 computers and run them simultaneously and that would make her able to recover your password in just one year. Keep that in mind when deciding whether your password is strong enough!.
If you want some tasks to be performed automatically each time after starting a Virtual Encrypted Disk, or right before stopping it, you can put an AutoRun file in the root folder of the Virtual Encrypted Disk, and USBCrypt would automatically execute that file for you each time you start or stop the Virtual Encrypted Disk.
To be used by USBCrypt in this manner, the file must have the name autorun, and it can have any extension allowed by Windows. Keep in mind that the extension of the file name determines what Windows does with it. For example, autorun.exe will be launched directly as any other program, autorun.bat would be executed by the command-line interpreter, and autorun.txt would be opened with Windows Notepad. And a file named autorun.inf has special processing rules, see below.
To be used by USBCrypt, the AutoRun file must be placed in the root folder of the Virtual Encrypted Disk. If there are several different AutoRun files in the root folder (for example, if both autorun.exe and autorun.bat are present), then only one of them will be executed by USBCrypt (and which one will be picked is generally unpredictable, so better have just one AutoRun file, to be sure about its execution).
If the AutoRun file is named anything but autorun.inf, USBCrypt executes such a file twice: once right after the Virtual Encrypted Disk is started (before opening the Windows Explorer window for it), and then right before stopping the Virtual Encrypted Disk. Note, however, that if you shut down the computer while a Virtual Encrypted Disk is running, then the AutoRun file is NOT executed before shutting down the computer. You must explicitly stop a Virtual Encrypted Disk for the AutoRun file to be launched before stopping.
When executing the AutoRun file, USBCrypt passes several command-line parameters to it that can be used by the AutoRun file to fine-tune its operation. For example, the autorun.bat file can access the parameters via the %1, %2, etc. variables as follows:
| Parameter | Value |
| %1 | Start when starting the Virtual Encrypted Disk, Stop when stopping it |
| %2 | The drive letter assigned to the Virtual Encrypted Disk |
| %3 | The drive letter of the host disk |
| %4 | The computer name |
| %5 | The user name, in double quotes |
| %6 | The domain name, in double quotes |
The AutoRun file can use the first parameter to perform different actions when starting or stopping the Virtual Encrypted Disk.
USBCrypt offers the option to run the AutoRun file "As Administrator". You should use this option with care and only if absolutely necessary.
If the AutoRun file is named autorun.inf, USBCrypt uses a different method of running it: it imitates the algorithm that Windows uses when it encounters such a file on a CD. Specifically, the autorun.inf file is only processed when the Virtual Encrypted Disk is started; this file is not used when stopping the disk. Secondly, the autorun.inf file is not executed directly; instead, USBCrypt looks for the SHELLEXECUTE statement the file may contain and launches the command that that statement specifies. If there is no such a statement in the autorun.inf file, USBCrypt attempts to launch the command specified in the OPEN statement instead. If OPEN statement is not present either, then USBCrypt stops processing the autorun.inf file and does not use any other statement the file may contain.
By default, USBCrypt prompts you to confirm the execution of the autorun file every time:
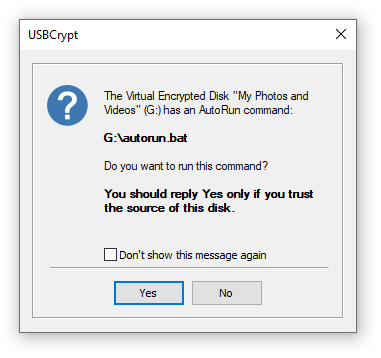
If you don't want to see this message again, you can select the Don't show this message again option, and press either Yes or No button: Pressing Yes would cause the autorun to always be executed in the future, while if you press No, it will never be executed again. If you change your mind, you can always change the execution permission later on, by clicking on the More options button when starting the Virtual Encrypted Disk. Note also, that this selection has an effect only when using this specific Virtual Encrypted Disk on this computer only: if you use a different Virtual Encrypted Disk that has an AutoRun file, or use this Virtual Encrypted Disk on another computer, you need to allow or deny the execution of its AutoRun file separately.
Sometimes when you attach an encrypted drive to your computer, you may see a message similar to the following:
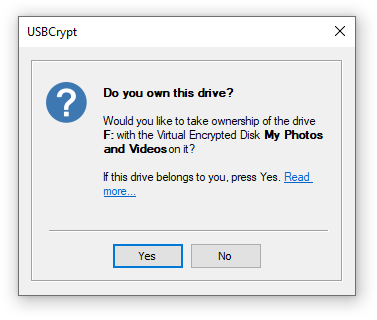
This message is shown if the USBCrypt license information on the encrypted drive is missing or does not match the USBCrypt license information on your computer. For example, if your friend brought her encrypted drive over to you and attached it to your computer, then obviously the license information on the drive would be different from the information that you have on your computer. Or, if you have attached an encrypted drive created with an evaluation version of USBCrypt: in such a case the encrypted drive would not have any license on it at all.
If the encrypted drive does not belong to you, reply No, and USBCrypt will leave the drive as it is now. However, if the drive does belong to you, press Yes, and USBCrypt will update the license information on the drive to match the current license on your computer. After that, you will not see this message again.
When you encrypt a removable drive with USBCrypt, you can use the encrypted drive not only with your own computer (where USBCrypt software has been installed), but also on other computers, that do not have USBCrypt software installed on them. This is possible because in addition to creating a Virtual Encrypted Disk on a removable drive, USBCrypt also places a portable version of its software on the drive, too, to make you able to use it on other computers.
Of course, in order to use your encrypted drive on another computer, that computer must run a compatible version of Windows: you cannot use the drive with a Windows 95/98 or a DOS computer. The Linux and Macintosh computers are not compatible with USBCrypt either. To be precise, you can attach an encrypted removable drive to such computers, but you would not be able to start the Virtual Encrypted Disk that is located on the removable drive.
When you connect an encrypted drive to a computer without USBCrypt software installed, you don't have the usual methods of immediately starting your Virtual Encrypted Disk: the USBCrypt icon does not appear on the taskbar immediately, and there is no USBCrypt icon on the Start menu to run it. Instead, you may see the usual screen displayed by Windows when a removable drive attached to the computer:

(The prompt may differ depending on the version of Windows that the computer has.) If you see the command to run USBCrypt off the removable drive, use it. If you see the command to open folder to view files (as shown above), you can use that command, and then double-click on USBCrypt (or USBCrypt.exe) icon when the folder window opens.
Keep in mind that it may take a few seconds for such a prompt to appear, be patient. If you don't see such a prompt after about 10 seconds or so, it could be that the auto-run feature is disabled on that computer. In such a case, use can start USBCrypt off the removable drive by navigating to it via the Start menu (by clicking on Computer or My Computer command that Start menu usually has.)
There are a few subtle but important differences between using the encrypted drive on a computer with and without USBCrypt software installed on it:
-
Administrator rights required to start USBCrypt off the encrypted drive
If you attach the encrypted drive to a computer that has no USBCrypt software installed on it, you may see a prompt asking you to allow USBCrypt software to run with the administrator's rights, such as this:
This message is a necessary security feature that is designed to reduce the risk of infecting the computer with the viruses. Contrary to what this message warns about, USBCrypt is not going to make changes to your computer, it only needs to load its encryption driver. Again, such a message appears only if you connect the encrypted drive to a computer without USBCrypt software installed on it, and the prompt appears only once per Windows session: once the administrator allows you to run USBCrypt off the encrypted drive, the prompt will not appear again until the computer is restarted.
Be sure to review the message before clicking Yes to allow USBCrypt to continue. If the messages warns you about an unknown program, do not continue and contact us if you need assistance.
Attention system administrators: we are offering a special Administrator's Kit that contains the USBCrypt software in the MSI format. You can use it to preinstall USBCrypt on the client computers, and thus eliminate the need for your users to request the administrator access each time.
-
The USBCrypt taskbar icon must exit in order to remove the encrypted drive safely
After you are all done working with the encrypted drive and stopped the Virtual Encrypted Disk it contains, one more step is necessary: click (or right-click) on the taskbar icon displayed by USBCrypt and choose Exit from the menu to close it:
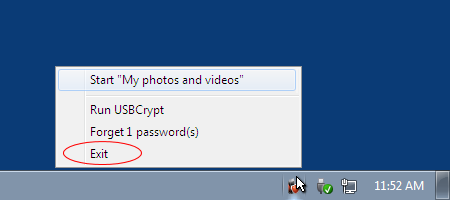
This step is necessary when USBCrypt is run from the encrypted drive itself, in order to stop the drive from being used by Windows. (This step is not necessary if USBCrypt is already installed on the computer). After you exit the USBCrypt taskbar icon, you can use the Safely Remove Hardware and Eject Media icon to disconnect the drive from the computer:
If you have created a large Virtual Encrypted Disk and put a large number of files into it that you open and save frequently, the encrypted file fragments may become scattered across all over the disk space and it may slow down the access to files. To improve on such a condition, Windows offers the option to optimize and defragment the files.
Keep in mind that when working with the encrypted files, there are two file systems in play: the file system within the Virtual Encrypted Disk, and also the file system of the host storage device. To achieve maximum optimization, both the host and the virtual file systems should be defragmented and optimized.
To optimize the host file system, it's a good practice to stop the Virtual Encrypted Disk hosted there first, to improve the optimization performance. Open This PC folder with File Explorer, select the host drive, right-click on it, choose Properties from the menu, and select the Tools tab. Finally, press the Optimize button to open the Optimize Drives screen that you can use to analyze the host drives and perform their optimization and defragmention.
After the host drive has been optimized, you may also want to optimize the file system within the Virtual Encrypted Disk. Instead of the procedure described above, you can use the built-in Windows command line tool Defrag.
First, start the Virtual Encrypted Disk, as usual, and then open Windows Terminal or command prompt As Administrator. Enter the Defrag command with the appropriate parameters to perform the optimization and defragmentation. For example, if you have started the Virtual Encrypted Disk with the drive letter X:, enter the command:
Defrag X:
The result of the optimization should be reported in the same window:
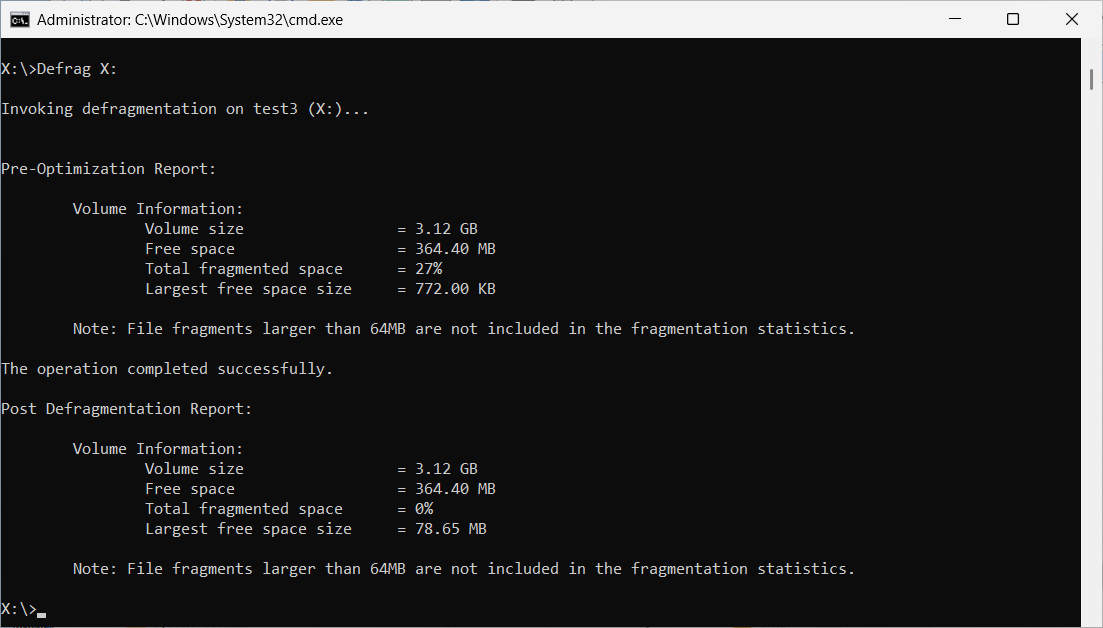
For more information on the Defrag command and the parameters it supports, enter at the command prompt:
Defrag /?
Please refer to the Windows documentation for more imnformation on the Defrag command.
After a Virtual Encrypted Disk has been created, you can increase or reduce its size using the Resize command. For example, if you want to add more files to the Virtual Encrypted Disk but the amount of the free space would not allow all new files to fit in, you need to expand the Virtual Encrypted Disk. (Of course, the host storage device must have sufficient free space to accommodate the expansion.) Or, if you find that you don't usually fill the Virtual Encrypted Disk completely with files and want to release the unused space back to the host device, you would compact (or shrink) the Virtual Encrypted Disk.
Note: not all Virtual Encrypted Disks can be resized: only the Virtual Encrypted Disks that have been formatted with the NTFS file system and that have not been split into file segments can be resized. If, when creating a Virtual Encrypted Disk, you have selected a file system other than NTFS, or if you have selected the option to split the host file into segments, such a Virtual Encrypted Disk cannot be resized. The only way to change the size of such a Virtual Encrypted Disk is to create a new Virtual Encrypted Disk of the desired new size, move the files from the old Virtual Encrypted Disk into the new one, and then delete the old Virtual Encrypted Disk.
Before starting the resizing procedure, close any application that might be using files from the Virtual Encrypted Disk. To redice the risk of data corruption, do not shut down or restart the computer, or open files from the Virtual Encrypted Disk until the resizing procedure is complete.
To resize a Virtual Encrypted Disk, run USBCrypt using its Desktop or Start Menu icon, select the host drive in the list, and press Next to go to the next screen. There, click More and choose the Resize Virtual Encrypted Disk command from the menu:
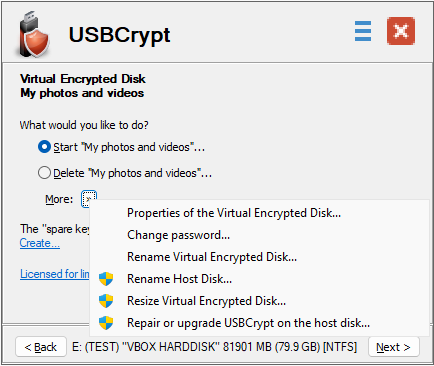
If you have not started the Virtual Encrypted Disk yet, you will be prompted to start it, as usual, by entering its password, and then continue with the Resize command.
The first step of the process depends on whether you plan on reducing or increasing the size of the Virtual Encrypted Disk:
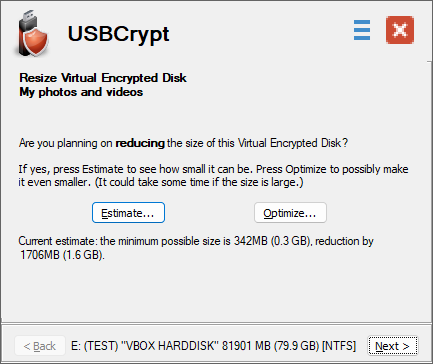
If you only want to expand the Virtual Encrypted Disk, press Next to continue to the next screen. However, if you plan on reducing (shrinking) the size the Virtual Encrypted Disk, press the Estimate button, and USBCrypt will analyze the file system layout of the Virtual Encrypted Disk to determine the amount of space by which it can be reduced. Understand that not all free space may be used for the shrinking, because the result depends on how the existing files within the Virtual Encrypted Disk are spread around the hosted media. If the Virtual Encrypted Disk is large and filled with a large number of files, this process may take a significant time.
You can also choose to perform the optimization of the free space to possibly reduce the size even more, by pressing the Optimize button. Again, if the Virtual Encrypted Disk is large and contains a large number of files, the optimization may take a long time, so you have the option to go ahead with the optimization or skip it and continue with the current estimate.
The final step is choosing the new size for the Virtual Encrypted Disk, using the screen similar to the following:
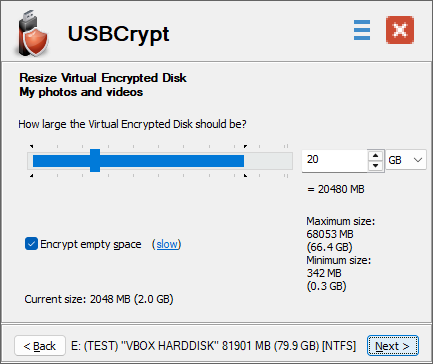
Use the slider for a rough selection of the desired size, and use the box next to the slider to enter the precise number for the new size. When expanding the Virtual Encrypted Disk, you can select the Encrypt empty space option if you want the newly allocated free space to be encrypted. (This option is ignored if you are shrinking the Virtual Encrypted Disk.) Remember that just like when creating a new Virtual Encrypted Disk, selecting this option may significantly increase the time of the resizing process. Read more...
After the resizing process is complete, the Virtual Encrypted Disk is immediately available for use with the new size.
If you have encrypted a drive with the Encryptability ![]() software, and would like to manage such a Virtual Encrypted Disk with USBCrypt software instead, you can convert the Virtual Encrypted Disk from Encryptability to USBCrypt format.
software, and would like to manage such a Virtual Encrypted Disk with USBCrypt software instead, you can convert the Virtual Encrypted Disk from Encryptability to USBCrypt format.
Before starting the conversion, first use Encryptability application to move the host folder or the Virtual Encrypted Disk to the target drive that you are going to use with USBCrypt. (Please refer to the Encryptability documentation for the information on how to move the host folders.) It makes no difference which folder on the target drive you move the Virtual Encrypted Disk into, it could be the root folder or one of the other folders the drive might have.
After moving the Virtual Encrypted Disk to the target storage device, run USBCrypt application (using its Desktop icon, for example), press the Tools button on the first screen:

Choose Convert from Encryptability from the menu to display the following screen:
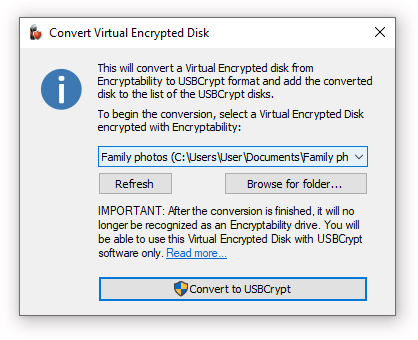
Select the Virtual Encrypted Disk you want to convert in the drop-down list. Or, if the Virtual Encrypted Disk is not listed, press Browse for folder and navigate to the host folder of the Virtual Encrypted Disk to convert. Finally, press the Convert to USBCrypt button to begin the conversion.
The conversion should take no more than a few seconds. After it's finished, Encryptability may display a message that a Virtual Encrypted Disk has been deleted, and a new USBCrypt notification icon should appear in the taskbar to represent the Virtual Encrypted Disk that has just been converted to USBCrypt format. Note that Encryptability will no longer recognize the drive as encrypted, and you should only use the USBCrypt application to start, stop, or manage the converted Virtual Encrypted Disk instead of Encryptability.
Can I convert the Virtual Encrypted Disk back to Encryptability?
Yes, but you need to use the Encryptability ![]() software to convert a Virtual Encrypted Disk from the USBCrypt to the Encryptability format. Please refer to the Encryptability documentation for more information about the process.
software to convert a Virtual Encrypted Disk from the USBCrypt to the Encryptability format. Please refer to the Encryptability documentation for more information about the process.
The USBCrypt Administrator's Kit is a set of tools designed to help system administrators with the deployment and management of USBCrypt on a large number of computers.
The kit contains the following files:
- The "enterprise build" of USBCrypt that does not require license validation over the Internet.
- The client installation packages of USBCrypt in the MSI format, to be used with the x86, x64, and ARM64 Windows clients.
- The Administrative Template file that contains the Group Policies supported by USBCrypt.
- The text of USBCrypt Volume License Agreement.
- The document describing the kit and how to use it.
The Administrative Template (.adm) file can be used with the Group Policies to deliver the license key of USBCrypt to the client computers without having to enter the license key manually on each computer. You can also use it to set up the restrictions for the USBCrypt users: for example, you can allow them to use the existing Virtual Encrypted Disks but prevent them from creating the new ones, or you can set up the policy for the password complexity to enforce when the users change the passwords, etc.
The USBCrypt Administrator's Kit is available as a separate download. Please contact us for more information or if you are interested in ordering the kit.

When you encrypt a host disk (such as drive H:) with USBCrypt, it uses a portion of the host disk to create a Virtual Encrypted Disk with its own drive letter (such as drive E:). The drive E: becomes available only after you have entered a valid password. Any file you put onto the drive E: will be encrypted and decrypted on-the-fly, in the background, as necessary.
What is a Virtual Encrypted Disk?
Virtual Encrypted Disk refers to the encrypted portion of the host disk that USBCrypt creates to keep your files secure. It's a "disk" because after you've entered your password, the encrypted area appears as a separate disk, with its own drive letter, different from the drive letter of the host disk. (Yes, you can choose the drive letter to be assigned to the Virtual Encrypted Disk.) It's "virtual" because there is no actual physical disk involved there. And it's "encrypted" because, well, it's encrypted.
What is a "host drive"?
Host drive is the actual physical drive that you use to "host" the Virtual Encrypted Disk.
How exactly does it do the encryption?
Please see a special web page that we've created to provide the technical details about our implementation of the encryption and other related algorithms: https://www.winability.com/go/?usbcrypt-encryption ![]()
Will the encrypted files be protected in the "safe mode" of Windows?
Yes, they will be protected no matter how you start Windows (in the safe mode or normally), or if someone were to remove the encrypted drive and attach it to another computer, even if another computer runs a different operating system (such as Linux). No matter what, your encrypted files will be protected until you enter the correct password. That's the power of strong encryption!
Does USBCrypt require the administrator rights?
Just like with most other software, the administrator rights are required to install USBCrypt on a computer. In addition, the administrator rights are also necessary in the following situations:
- To encrypt a drive for the first time and create a Virtual Encrypted Disk on it, as well as to delete the Virtual Encrypted Disk, or upgrade the USBCrypt software on it, if necessary.
- To use an encrypted drive on a computer that does not have USBCrypt software already installed on it.
However, to use the encrypted drives on your own computer(s) where you have already installed USBCrypt software, the administrative rights are NOT required.
Is there a limit to how many drives I can encrypt with USBCrypt?
No, there is no such a limit, provided that you only encrypt the drives that belong to you or to your organization, and you do not distribute the encrypted drives to any third party. If your friends or associates want to encrypt their own drives, please let them purchase their own copies of USBCrypt. If you have an idea for a business that involves encrypting drives for your customers, a separate license must be obtained. Please contact us to discuss the possibilities.
How do I check the encrypted drive for errors?
If you suspect something is wrong with the drive encrypted with USBCrypt, the first thing to do is check the host drive for errors:
- Stop the Virtual Encrypted Disk, if necessary;
- Open the This PC (or Computer) folder and right-click on the host drive;
- Choose Properties from the menu, select the Tools tab;
- Use the Error checking area to check the drive for errors.
You can also run the chkdsk command line utility, as with any other drive. When selecting the error checking options, you may want to choose to scan the drive for bad sectors.
After the host drive has been checked, you may want to check the Virtual Encrypted Disk for errors, too: first, start the Virtual Encrypted Disk as usual, and then use the same steps shown above, but this time right-click on the drive letter that belongs to the Virtual Encrypted Disk, rather than the host disk. It's not necessary to scan the Virtual Encrypted Disk for bad sectors, because scanning the host drive should have been sufficient for that.
Is there a "back door" in USBCrypt?
USBCrypt gives you an option to create a "back door" for your own use, it's called the spare key file. If you select this option while creating a Virtual Encrypted Disk, USBCrypt will store a special file on your computer that you can use later on as a "back door" to reset the password in case you forget it. We stress that this "back door" remains on your computer, not anywhere else. Only you (or someone who gets access to your computer) would be able to use this "back door".
There is no any other "back door" in USBCrypt. It means that if you forget your password, neither we nor anyone else will be able to help you.
I've lost USBCrypt password. What should I do?
If you've created a "spare key" file for your encrypted disk, you can use it to reset the password. Note that each encrypted disk must have a separate "spare key" created specifically for it. If you did not create the "spare key" file, then the only way to recover your password is by trying every possible combination of the password characters. Of course, if you've chosen a strong password and then forgotten it, the recovery process can take a very long time, so don't count on it as a reliable way of getting access to your encrypted files.
Will my anti-virus program protect files on the encrypted disk?
If you have not entered your password yet (and the Virtual Encrypted disk has not started) then all the files and folders it contains remain completely inaccessible to any program, including anti-virus. (The viruses cannot infect your encrypted files, either). After you've entered your password and started the Virtual Encrypted Disk, it becomes available to all programs, including anti-virus (and viruses!), just like any other regular disk. Unless you have excluded the Virtual Encrypted Disk from your anti-virus software, then it should be protected by the anti-virus, like any other disk.
Will my backup program back up the files located on the encrypted disk?
If the Virtual Encrypted Disk has not started, then you can backup the host disk, and that should backup the files of the Virtual Encrypted Disk, too. (They will remain encrypted in the backup set). If the Virtual Encrypted Disk has started, then you can backup individual files or folders that it contains, just like on a regular disk. Be aware, however, that in this case the files will be backed up in their plain, decrypted state.
How do I use Windows Backup with the encrypted drive?
Windows Backup software that comes with Windows 7 or Windows Vista is very picky about the drives to backup your files to. To make it recognize your encrypted drive as a valid backup destination, you need to choose the NTFS file system for the Virtual Encrypted Disk when encrypting the drive, and also start it as a removable drive. (You can select this option by clicking on the More Options button when starting the disk). Even then, it may not let you backup the system image to such a drive. If you must backup the system image to an encrypted drive, you may want to use some other backup software that recognizes the encrypted drives as the valid backup destinations.
How do I enter the License Key?
Run USBCrypt off the Start menu or desktop and click on the link Licensed for limited evaluation use only. This should open the About USBCrypt window. Press the Enter License Key button and enter your license information into the form.
Or, click on the question mark button in the right-top corner of the USBCrypt window, and choose the Enter License Key command from the menu, then and enter your license information into the form.
IMPORTANT: When entering your license information, make sure you enter your name, number of computers, and the license key exactly as they are shown on your license certificate, including all capitalization and punctuation. Otherwise, USBCrypt may not accept the license key or may not register your information properly. You may wish to copy and paste the name and key from our message into the form, to avoid typos.
Will I need to re-encrypt the drives I encrypted during the trial?
No, there is no need to re-encrypt the drives that you've encrypted during the trial period. After you have purchased ![]() a license for continued use and entered your license key into the software, it will automatically upgrade your encrypted drives for the full use, with the strong password protection. (It will ask you to confirm this action next time you start the Virtual Encrypted Disk.)
a license for continued use and entered your license key into the software, it will automatically upgrade your encrypted drives for the full use, with the strong password protection. (It will ask you to confirm this action next time you start the Virtual Encrypted Disk.)
What happens when the evaluation period expires?
This software comes with a built-in license that allows you to use it for free for the first 30 days after the installation. When this initial evaluation period expires, you can still run USBCrypt, but you cannot use it to encrypt any new drives. Also, you can start the previously encrypted drives in the write-protected mode only. This should allow you to extract your existing files out of the encrypted disks, but you won't be able to save the modifications back to them. The full functionality of USBCrypt is restored immediately when you purchase ![]() a license for its continued use and enter your license key into the program.
a license for its continued use and enter your license key into the program.
Can I use the same license key to install USBCrypt on several computers?
Yes, you can use the same license key, provided that you are installing it on no more computers than included in your license. Please refer to the file License.txt (installed along with other files of USBCrypt) for the detailed description of the terms of using this software on more than one computer. For information on our site license and quantity discounts, please visit our Online Store ![]() .
.
May I give a copy of USBCrypt software to a friend?
Yes, you may give the installation files of our programs to your friends and associates. However, you may NOT share your license key, if any, with anybody else. Please remember that the license key we provide you with are for your own use only. If your friends like our programs, please let them purchase their own license keys. To avoid possible confusion, please give out the original installation files that you may download from our web site.
There are several other simple, but important conditions which we impose on further redistribution of our products. Please refer to the file License.txt in the folder where you have installed USBCrypt for the complete description of our distribution requirements.
I've upgraded USBCrypt to a newer version. Will it read the encrypted files I created with the previous version?
Yes, USBCrypt is backward-compatible: the new versions can read the files encrypted with the old versions of USBCrypt. Note that the opposite is not necessarily true: sometimes we make improvements in the new version such that they are not recognized by the older versions of USBCrypt. For example, USBCrypt version 13.x uses a new format for the Virtual Encrypted Disks, that was not in existence when the versions 10.x of USBCrypt were released. As a result, if you attempt to use a drive encrypted with USBCrypt version 13.x on a computer that has only USBCrypt version 10.x installed, such a drive may not be recognized as a valid encrypted drive and your password may not be accepted even if you've entered it correctly. A solution to such a problem is simple: install the newer version of USBCrypt on the computer and it should be able to recognize the new format of the encrypted drive and accept your password.
Why does USBCrypt ask me to update software on the host disk?
If you've installed a newer version of USBCrypt on your computer and then connected a removable drive previously encrypted with an older version, USBCrypt may display a prompt asking you for a permission to update software on the host disk. This is happening because USBCrypt puts a portable version of it onto the encrypted disk, to make you able to use the disk with other computers that don't have USBCrypt installed on them. (When you connect the encrypted drive to such a computer, you can run the portable version of USBCrypt directly off the host disk, without the need to install a separate copy of USBCrypt on that computer.)
So, when you see a prompt asking you to update software on the host disk, if you reply Yes, USBCrypt will simply replace the portable version of it on the removable disk with the new version. After that, you should not see such a prompt any more.
Why does USBCrypt ask me to adjust the security attributes of the host drive?
When you format a drive in Windows with the NTFS file system, it makes some assumptions about the intended use of the drive which may not match your actual intentions. For example, if the drive is fixed (rather than removable), Windows assumes that you are going to use the drive permanently attached to your computer. As a result, it creates the security attributes for the drive so that only your user account has the full access to it, and it restricts access to the drive for other users.
This may cause a problem in case you decide to detach the drive from your computer and attach it to some other computer, which does not have your user account on it. With the default security attributes, you would not have access to the drive on that computer and would not be able to start the Virtual Encrypted Disk off it!
To prevent such situations from happening, when encrypting a drive, USBCrypt analyses its security attributes and if it detects that they may prevent you from using the drive on other computers, it asks you to make the adjustments. If you do plan on using the drive with other computers, reply Yes to allow the adjustments, and USBCrypt will make them for you.
Which file system should I choose for the encrypted files?
When choosing the size for a new Virtual Encrypted Disk, you can also choose the file system to be used to organize files within the Virtual Encrypted Disk: FAT32, exFAT, or NTFS. Each file system has advantages and disadvatages:
FAT32 - the simplest file system with a minimum overhead. Its main limitation is that it cannot store files larger than 4GB, so it's suitable for storing relatively small files only. Also, the FAT32 Virtual Encrypted Disks cannot be resized after they have been created.
exFAT - this system does not have a limit on the size of the files it can store, but it does not offer most of the advaced features like the NTFS file system does. The exFAT does NOT allow resizing of Virtual Encrypted Disks after they have been created.
NTFS - the most advanced system that offers the complete set of file management capabilities supported by Windows. It does not have a limit on the size of the files it can store. Also, only Virtual Encrypted Disk with the NTFS file system can be resized after they have been created.
How does the Encrypt Empty Space option affect the security of my files?
The Encrypt Empty Space option does not affect the security of your files: they are always encrypted and protected whether this option is enabled or not. What it does is it only affects whether the empty space of the Virtual Encrypted Disk is encrypted or not, when you first create it.
This option greatly affects the speed of creation of the Virtual Encrypted Disk. If this option is selected, then USBCrypt will encrypt the empty space of the Virtual Encrypted Disk, even if it's initially not used to hold any useful information. The process of such encryption can take a rather long time, if the host drive is very large. For example, encrypting a 2TB (two terabytes or 2048 gigabytes) SATA drive connected via the SATA interface to a modern consumer-grade computer can take approximately 10 hours to complete.
However, if you clear the Encrypt empty space option, then USBCrypt will allocate the empty space from the available space of the host drive without encrypting it. Such an operation can be performed significantly faster: creating the same 2TB drive can now take less than a minute! The price for such an increase in the speed is, of course, that the empty space will not be encrypted. However, as you start adding files and folders to such a drive, they will be encrypted, as usual.
How important is it to have the empty space encrypted? It depends on whether you want the adversary to be able to deduce some aggregate information about your encrypted data. For example, by analyzing the raw sectors of data allocated on the host drive, the adversary may be able to tell which portions of your Virtual Encrypted Disk image contain encrypted data and which contain the empty space. From that, the adversary could deduce, for example, whether your encrypted drive is almost empty, or almost full. By analyzing the distribution of the encrypted sectors and the unencrypted empty sector within the Virtual Encrypted Disk image, the adversary can probably guess the type of the file system the Virtual Encrypted Disk has. However, in no case the adversary will be able to get to your actual files or folders or any information about them: they are encrypted as strong as ever, no matter whether the Encrypt empty space option was selected or not.
Ultimately, it's for you to decide whether it's acceptable for the adversary to be able to detect how much of your Virtual Encrypted Disk is empty and whether preventing that is worth sacrificing the significant increase in the speed of the creation of the Virtual Encrypted Disk.
Note that not all versions of Windows allow to clear the Encrypt empty space option for some file systems. For example, at the time of this writing, Windows XP does not allow to clear this option if the host drive is formatted with the FAT or FAT32 file system. Or, this option can't be cleared for the NTFS disks with the compression enabled. If USBCrypt detects such a condition, it disables this option to prevent you from using it when it's not supported by your computer.
Why the NTFS compression or EFS encryption should not be used with the USBCrypt files?
The NTFS file system allows one to enable the data compression and/or encryption for the files stored on it. However, neither NTFS compression nor the EFS encryption should be enabled for the files that USBCrypt uses to store the Virtual Encrypted Disk image on the host disk. The reason for that is simple:
- The EFS encryption would be redundant: the data stored on the NTFS host disk is already encrypted with USBCrypt. Encrypting them again with EFS would not add additional protection to your data: the encryption performed by USBCrypt is already strong enough. Therefore, enabling the EFS encryption would only create additional work for the computer CPU, slowing the process down.
- The usual compression methods are effective only for the highly structured or repetitive data. They are not effective for the encrypted data. Enabling the NTFS compression would waste the CPU cycles for no good reason.
For these reasons, USBCrypt disables the NTFS compression and EFS encryption for the files it uses to store the Virtual Encrypted Disk image.
I've encrypted a drive and now Windows is showing the 'Low Disk Space' balloons. Why?
If, while encrypting a drive for the first time, you've chosen the size of the Virtual Encrypted Disk to fill up all available free space of the host disk, then after the encryption is finished, very little unencrypted free space will remain on the host disk. (Because all such space will now be reserved for the encrypted files.) Windows is designed so that if it detects that the free space on any disk decreases below a certain level, it displays a notification in the form of a popup "balloon" in the taskbar notification area. If you don't want to see such notifications, you can use the Tools button on the main screen of USBCrypt to suppress them (or to restore them back later on). Unfortunately, Windows does not let one suppress the notifications for some drives and allow them for others, so if you suppress them, keep in mind that there will be no notification if the free space on some other drive (such as the main C: drive) decreases below the minimum level.
I've shared a Virtual Encrypted Disk on a network, but Windows denies access to it from other computers?
If you have started the Virtual Encrypted Disk as a removable drive, and shared that drive on your local network, then Windows may display an Access denied message when attempting to open the shared drive from another computer. If you experience this problem, try to stop the Virtual Encrypted Disk, and then start it again, but this time choose to start it as a fixed drive. (You can change the type of the drive by clicking on the More Options... button when starting the disk, on the same screen where you enter its password.) If you share the fixed drive on the network, you should be able to open it from other computers without a problem.
I'm trying to use the Create System Image command of Windows, but it shows an error?
Apparently, Windows backup program gets confused when it encounters a Virtual Encrypted Disk while searching for a disk suitable for holding the system image. Instead of silently skipping the disk that it does not quite understand, it displays an error message with the error code 0x81000036, and it does not let you select the destination disk for the system image. To work around such a problem, simply stop any Virtual Encrypted Disk that you might have previously started, and then try to use the Create System Image command of Windows again. After the command is complete, start the Virtual Encrypted Disk back.
How can I get a printed version of this guide?
This user's guide is available online in the printer-friendly format:
https://www.winability.com/usbcrypt/users-guide-printable.htm ![]()
Open the link above in your web browser and use the web browser's Print command to print it out on your printer.