FAQ (Frequently Asked Questions) |
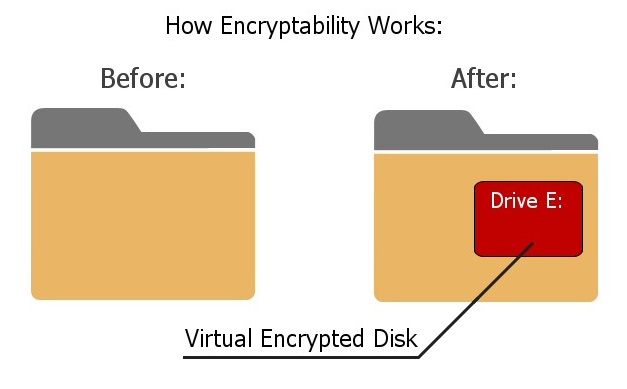
Encryptability works by creating a Virtual Encrypted Disk inside the host folder and protecting it with the password of your choosing. The Virtual Encrypted Disk (such as drive E:) becomes available only after you have entered a valid password. Any file you put onto the drive E: will be encrypted and decrypted on-the-fly, in the background, as necessary. When you no longer need to work with the private files, stop the Virtual Encrypted Disk and its drive letter (E:) will be removed and your files will become locked with the password again, until next time you want to work with them.
Virtual Encrypted Disk refers to the encrypted portion of the host disk that Encryptability creates to keep your files secure. It's a "disk" because after you've entered your password, the encrypted area appears as a separate disk, with its own drive letter, different from the drive letter of the host disk. (Yes, you can choose the drive letter to be assigned to the Virtual Encrypted Disk.) It's "virtual" because there is no actual physical disk involved there. And it's "encrypted" because, well, it's encrypted.
Host folder is a regular folder on one of the physical storage devices where Encryptability stores the files related to a particular Virtual Encrypted Disk. There are usually several such files, used to store the encryption key, as well as the encrypted data. You can see the contents of the host folder by selecting the Virtual Encrypted Disk in the list of the Encryptability application and choosing File - More - Open host folder location. Please be careful not to delete, rename, or otherwise change any file in that folder, because doing so may corrupt the encrypted data and prevent you from using the files stored in the Virtual Encrypted Disk. Note that each host folder may contain only the files belonging to one Virtual Encrypted Disk; if you decide to move files that belong to several Virtual Encrypted Disks into the same host folder, it may confuse the Encryptability application and prevent you from opening such Virtual Encrypted Disks.
Please see a special web page that we've created to provide the technical details about our implementation of the encryption and other related algorithms: https://www.winability.com/go/?encryptability-encryption ![]()
No, Encryptability does not have a portable version. However, we offer another encryption product, USBCrypt ![]() , that does offers a portable version of its software and is specifically designed to better handle the encryption of the removable drives.
, that does offers a portable version of its software and is specifically designed to better handle the encryption of the removable drives.
Yes, they will be protected no matter how you start Windows (in the safe mode or normally), or if someone were to remove the encrypted drive and attach it to another computer, even if another computer runs a different operating system (such as Linux). No matter what, your encrypted files will be protected until you enter the correct password. That's the power of strong encryption!
Just like with most other software, the administrator rights are required to install Encryptability on a computer. In addition, the administrator rights are also necessary for several operations, such as creating a new Virtual Encrypted Disk, deleting an existing Virtual Encrypted Disk, or moving a Virtual Encrypted Disk to a different location.
However, the administrative rights are NOT required to actually use the Virtual Encrypted Disks, that is to start, stop, rename, change passwords, etc.
No, there is no such a limit, provided that you only create them for use by yourself (or by your organization, if you have purchased a business license), and you do not distribute the Virtual Encrypted Disks to any third party. If your friends or associates want to have their own Virtual Encrypted Disks, please let them purchase their own copies of Encryptability. If you have an idea for a business that involves providing Virtual Encrypted Disks to your customers, a separate license must be obtained. Please contact us to discuss the possibilities.
If you suspect something is wrong with Virtual Encrypted Disk created with Encryptability, the first thing to do is check the host drive for errors:
You can also run the chkdsk command line utility, as with any other drive. When selecting the error checking options, you may want to choose to scan the drive for bad sectors.
After the host drive has been checked, you may want to check the Virtual Encrypted Disk for errors, too: first, start the Virtual Encrypted Disk as usual, and then use the same steps shown above, but this time right-click on the drive letter that belongs to the Virtual Encrypted Disk, rather than the host disk. It's not necessary to scan the Virtual Encrypted Disk for bad sectors, because scanning the host drive should have been sufficient for that.
Encryptability gives you an option to create a "back door" for your own use, it's called the spare key file. If you select this option while creating a Virtual Encrypted Disk, Encryptability will store a special file on your computer that you can use later on as a "back door" to reset the password in case you forget it. We stress that this "back door" remains on your computer, not anywhere else. Only you (or someone who gets access to your computer) would be able to use this "back door".
There is no any other "back door" in Encryptability. It means that if you forget your password, neither we nor anyone else will be able to help you.
If you've created a "spare key" file for your encrypted disk, you can use it to reset the password. Note that each encrypted disk must have a separate "spare key" created specifically for it. If you did not create the "spare key" file, then the only way to recover your password is by trying every possible combination of the password characters. Of course, if you've chosen a strong password and then forgotten it, the recovery process can take a very long time, so don't count on it as a reliable way of getting access to your encrypted files.
If you have not entered your password yet (and the Virtual Encrypted disk has not started) then all the files and folders it contains remain completely inaccessible to any program, including anti-virus. (The viruses cannot infect your encrypted files, either). After you've entered your password and started the Virtual Encrypted Disk, it becomes available to all programs, including anti-virus (and viruses!), just like any other regular disk. Unless you have excluded the Virtual Encrypted Disk from your anti-virus software, then it should be protected by the anti-virus, like any other disk.
If the Virtual Encrypted Disk has not started, then you can backup the host disk, and that should backup the files of the Virtual Encrypted Disk, too. (They will remain encrypted in the backup set). If the Virtual Encrypted Disk has started, then you can backup individual files or folders that it contains, just like on a regular disk. Be aware, however, that in this case the files will be backed up in their plain, decrypted state.
Windows Backup software is very picky about the drives to backup your files to. To make it recognize your encrypted drive as a valid backup destination, you need to choose the NTFS file system for the Virtual Encrypted Disk when encrypting the drive, and also start it as a removable drive. (You can select this option by clicking on the More Options button when starting the disk). Even then, it may not let you backup the system image to such a drive. If you must backup the system image to an encrypted drive, you may want to use some other backup software that recognizes the encrypted drives as the valid backup destinations.
Run Encryptability off the Start menu or desktop and click on the link Licensed for limited evaluation use only. This should open the About Encryptability window. Press the Enter License Key button and enter your license information into the form.
Or, use the Help - Enter License Key command from the menu of the Encryptability window, and then enter your license information into the form.
IMPORTANT: When entering your license information, make sure you enter your name, number of computers, and the license key exactly as they are shown on your license certificate, including all capitalization and punctuation. Otherwise, Encryptability may not accept the license key or may not register your information properly. You may wish to copy and paste the name and key from our message into the form, to avoid typos.
No, there is no need to re-encrypt the drives that you've encrypted during the trial period. After you have purchased ![]() a license for continued use and entered your license key into the software, it will automatically upgrade your encrypted drives for the full use, with the strong password protection. (It will ask you to confirm this action next time you start the Virtual Encrypted Disk.)
a license for continued use and entered your license key into the software, it will automatically upgrade your encrypted drives for the full use, with the strong password protection. (It will ask you to confirm this action next time you start the Virtual Encrypted Disk.)
This software comes with a built-in license that allows you to use it for free for the first 30 days after the installation. When this initial evaluation period expires, you can still run Encryptability, but you cannot use it to create any new Virtual Encrypted Disks. Also, you can start the previously encrypted drives in the write-protected mode only. This should allow you to extract your existing files out of the encrypted disks, but you won't be able to save the modifications back to them. The full functionality of Encryptability is restored immediately when you purchase ![]() a license for its continued use and enter your license key into the program.
a license for its continued use and enter your license key into the program.
Yes, you can use the same license key, provided that you are installing it on no more computers than included in your license. Please refer to the file License.txt (installed along with other files of Encryptability) for the detailed description of the terms of using this software on more than one computer. For information on our site license and quantity discounts, please visit our Online Store ![]() .
.
Yes, you may give the installation files of our programs to your friends and associates. However, you may NOT share your license key, if any, with anybody else. Please remember that the license key we provide you with are for your own use only. If your friends like our programs, please let them purchase their own license keys. To avoid possible confusion, please give out the original installation files that you may download from our web site.
There are several other simple, but important conditions which we impose on further redistribution of our products. Please refer to the file License.txt in the folder where you have installed Encryptability for the complete description of our distribution requirements.
Yes, Encryptability is backward-compatible: the new versions can read the files encrypted with the old versions of Encryptability. (Note that the opposite is not necessarily true: sometimes we make improvements in the new version such that they are not recognized by the older versions of Encryptability.)
When choosing the size for a new Virtual Encrypted Disk, you can also choose the file system to be used to organize files within the Virtual Encrypted Disk: FAT32, exFAT, or NTFS. Each file system has advantages and disadvatages:
FAT32 - the simplest file system with a minimum overhead. Its main limitation is that it cannot store files larger than 4GB, so it's suitable for storing relatively small files only. Also, the FAT32 Virtual Encrypted Disks cannot be resized after they have been created.
exFAT - this system does not have a limit on the size of the files it can store, but it does not offer most of the advaced features like the NTFS file system does. The exFAT does NOT allow resizing of Virtual Encrypted Disks after they have been created.
NTFS - the most advanced system that offers the complete set of file management capabilities supported by Windows. It does not have a limit on the size of the files it can store. Also, only Virtual Encrypted Disk with the NTFS file system can be resized after they have been created.
The Encrypt Empty Space option does not affect the security of your files: they are always encrypted and protected whether this option is enabled or not. What it does is it only affects whether the empty space of the Virtual Encrypted Disk is encrypted or not, when you first create it, or when you expand the Virtual Encrypted Disk with the Resize command.
This option greatly affects the speed of creation of the Virtual Encrypted Disk. If this option is selected, then Encryptability will encrypt the empty space of the Virtual Encrypted Disk, even if it's initially not used to hold any useful information. The process of such encryption can take a rather long time, if the host drive is very large. For example, encrypting a 2TB (two terabytes or 2048 gigabytes) SATA drive connected via the SATA interface to a modern consumer-grade computer can take approximately 10 hours to complete.
However, if you clear the Encrypt empty space option, then Encryptability will allocate the empty space from the available space of the host drive without encrypting it. Such an operation can be performed significantly faster: creating the same 2TB drive can now take less than a minute! The price for such an increase in the speed is, of course, that the empty space will not be encrypted. However, as you start adding files and folders to such a drive, they will be encrypted, as usual.
How important is it to have the empty space encrypted? It depends on whether you want the adversary to be able to deduce some aggregate information about your encrypted data. For example, by analyzing the raw sectors of data allocated on the host drive, the adversary may be able to tell which portions of your Virtual Encrypted Disk image contain encrypted data and which contain the empty space. From that, the adversary could deduce, for example, whether your encrypted drive is almost empty, or almost full. By analyzing the distribution of the encrypted sectors and the unencrypted empty sectors within the Virtual Encrypted Disk image, the adversary can probably guess the type of the file system the Virtual Encrypted Disk has. However, in no case the adversary will be able to get to your actual files or folders or any information about them: they are encrypted as strong as ever, no matter whether the Encrypt empty space option was selected or not.
Ultimately, it's for you to decide whether it's acceptable for the adversary to be able to detect how much of your Virtual Encrypted Disk is empty and whether preventing that is worth sacrificing the significant increase in the speed of the creation of the Virtual Encrypted Disk.
Note that not all versions of Windows allow to clear the Encrypt empty space option for some file systems. For example, at the time of this writing, Windows does not allow to clear this option if the host drive is formatted with the FAT or FAT32 file system. Or, this option can't be cleared for the NTFS disks with the compression enabled. If Encryptability detects such a condition, it disables this option to prevent you from using it when it's not supported by your computer.
The NTFS file system allows one to enable the data compression and/or encryption for the files stored on it. However, neither NTFS compression nor the EFS encryption should be enabled for the files that Encryptability uses to store the Virtual Encrypted Disk image on the host disk. The reason for that is simple:
For these reasons, Encryptability disables the NTFS compression and EFS encryption for the files it uses to store the Virtual Encrypted Disk image.
If you have started the Virtual Encrypted Disk as a removable drive, and shared that drive on your local network, then Windows may display an Access denied message when attempting to open the shared drive from another computer. If you experience this problem, try to stop the Virtual Encrypted Disk, and then start it again, but this time choose to start it as a fixed drive. (You can change the type of the drive by clicking on the More Options... button when starting the disk, on the same screen where you enter its password.) If you share the fixed drive on the network, you should be able to open it from other computers without a problem.
Apparently, Windows backup program gets confused when it encounters a Virtual Encrypted Disk while searching for a disk suitable for holding the system image. Instead of silently skipping the disk that it does not quite understand, it displays an error message with the error code 0x81000036, and it does not let you select the destination disk for the system image. To work around such a problem, simply stop any Virtual Encrypted Disk that you might have previously started, and then try to use the Create System Image command of Windows again. After the command is complete, start the Virtual Encrypted Disks again.
Yes, you can select a mapped network drive or a shared network folder as the location for a Virtual Encrypted Disk when creating or moving it, however you should consider the risk of a possible data loss or corruption in such a situation. If the other computer where the hosted network folder is physically located (the server) is shut down, or restarted, or the network connection to that computer gets disrupted while the Virtual Encrypted Disk is operating, the normal flow of data between your computer and the server is disrupted. (The same disruption occurs when a local host drive malfunctions.) If you save a file to the Virtual Encrypted Disk under such a condution, the program you use may report that the file has been saved successfully, but when Encryptability attempts to send the encrypted data over the network to store it on the server, an error occurs and the data may be lost.
When Encryptability detects such a situation, it attempts to correct the problem by offering you to restart the Virtual Encrypted Disk after the connection to the network location is restored. After that, you should save any open documents you store in the Virtual Encrypted Disk to make sure no changes were lost during the network disruption.
Make sure you have a good backup procedure in place to keep a copy of your important data on a separate physical storage device and keep the backup set up to date. If you have a good backup, it can help minimize the loss of useful data in case of a network or hardware falure.
This user's guide is available online in the printer-friendly format:
https://www.winability.com/encryptability/users-guide-printable.htm ![]()
Open the link above in your web browser and use the web browser's Print command to print it out on your printer.